Introduction
Cloud Access Security Brokers (CASBs) have become integral in ensuring the security and compliance of cloud environments. As organizations increasingly adopt cloud services, CASBs play a crucial role in extending security controls to cloud applications and data. This document provides an overview of CASBs, their purpose, and their use cases in modern cloud security strategies.
What is CASB?
A CASB is a security solution that acts as an intermediary between users and cloud service providers, providing visibility, control, and security for cloud-based applications. It sits between users/devices and cloud applications to enforce security policies, detect threats, and ensure compliance.
There are Four Pillars of CASB:
1. Visibility and Control
CASBs offer visibility into cloud usage, including sanctioned and unsanctioned (shadow IT) applications. They enable administrators to monitor user activities, data flows, and enforce security policies across cloud services.
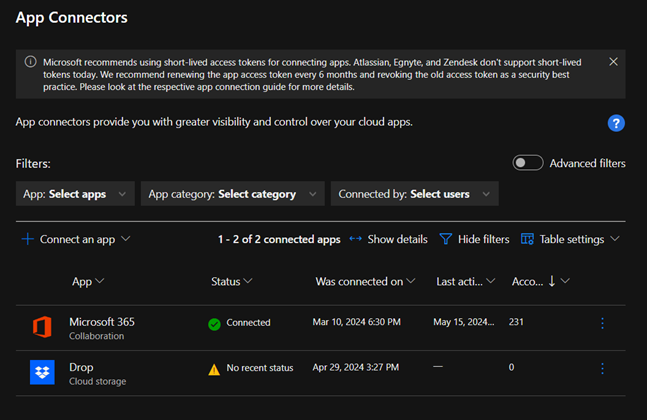
Connect apps:
- In the Microsoft Defender Portal, select Settings. Then choose Cloud Apps.
- Under Connected Apps, select App Connectors.
- Select the +Connect an app to add an app and then select an app.
- Follow the configuration steps to connect the app.
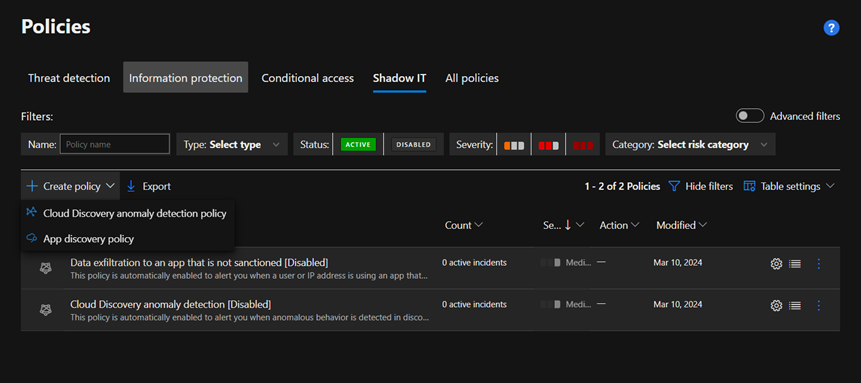
Cloud Discovery anomaly detection policy enables you to set up and configure continuous monitoring of unusual increases in cloud application usage. Increases in downloaded data, uploaded data, transactions, and users are considered for each cloud application.
- Alert when anomalous behavior is detected in discovered users and apps, such as: large amounts of uploaded data compared to other users, large user transactions compared to the user’s history.
- Alert when anomalous behavior is detected in discovered IP addresses and apps, such as: large amounts of uploaded data compared to other IP addresses, large app transactions compared to the IP address’s history.
Discovery policies enable you to set alerts that notify you when new apps are detected within your organization.
2. Data Protection
CASB provides out of box capabilities to monitor access to data stored on cloud.
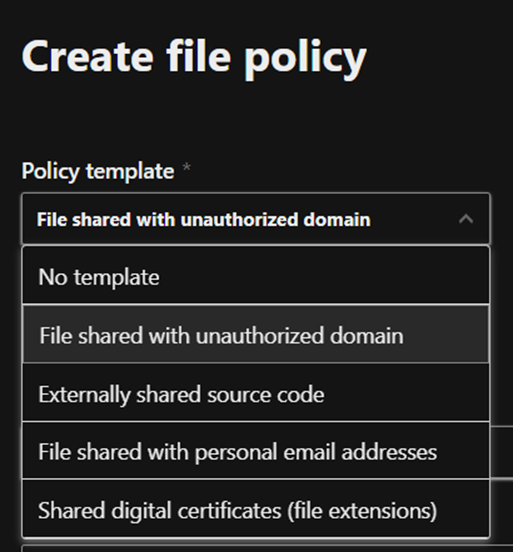
3. Threat Detection and Response
CASB provides various alerts to inform the IT about threats that are detected within the organization users based on malware scanning, anomaly detection, and user’s behavior.
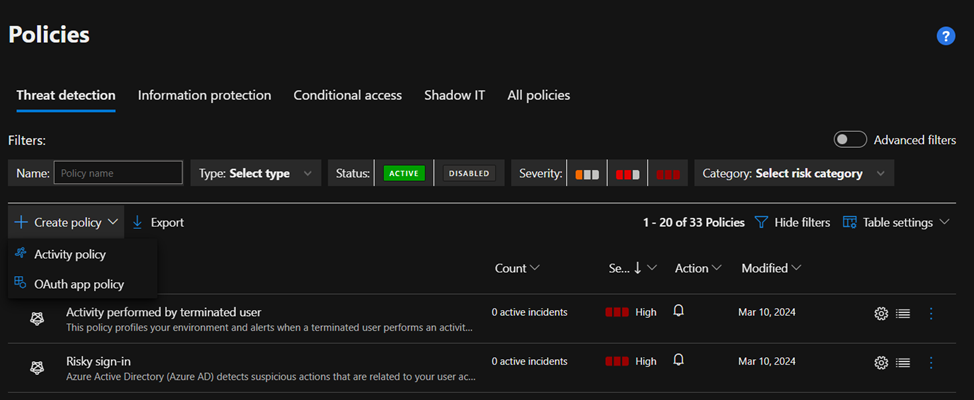
Activity policy is an API-based policy that enables you to monitor your organization’s activities in the cloud.
OAuth app policies enable you to investigate which permissions each app requested and which users authorized them for Microsoft 365, Google Workspace, and Salesforce.
4. Compliance Enforcement
CASBs help organizations comply with regulatory requirements and industry standards (such as GDPR, HIPAA) by monitoring data in the cloud, enforcing policies, and generating compliance reports and alerts.
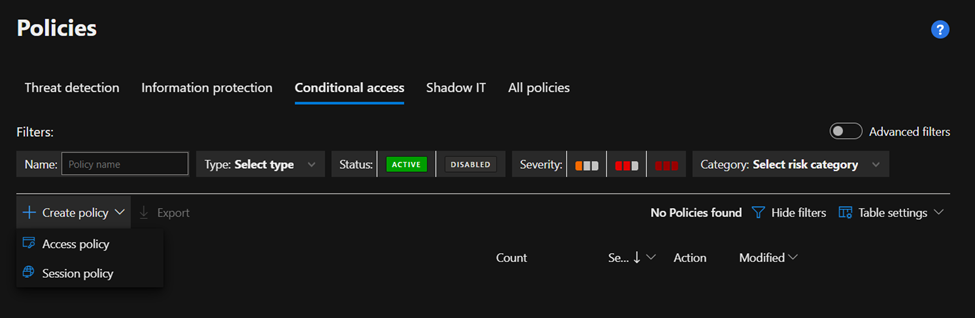
Access policies enable real-time monitoring and control over access to cloud apps based on user, location, device, and app.
Session policies provide granular visibility into cloud apps with real-time, session-level monitoring.
Benefits of Using CASBs
- Enhanced Security: Extends security controls to cloud environments, reducing risks associated with cloud adoption.
- Data Protection: Ensures confidentiality, integrity, and availability of data in the cloud.
- Compliance: Helps meet regulatory requirements and industry standards.
- Visibility and Control: Provides granular visibility into cloud usage and enforces policies consistently.
In this guide there are use cases for CASBs that I recommend as a baseline for a successful implementation to improve your cloud security.
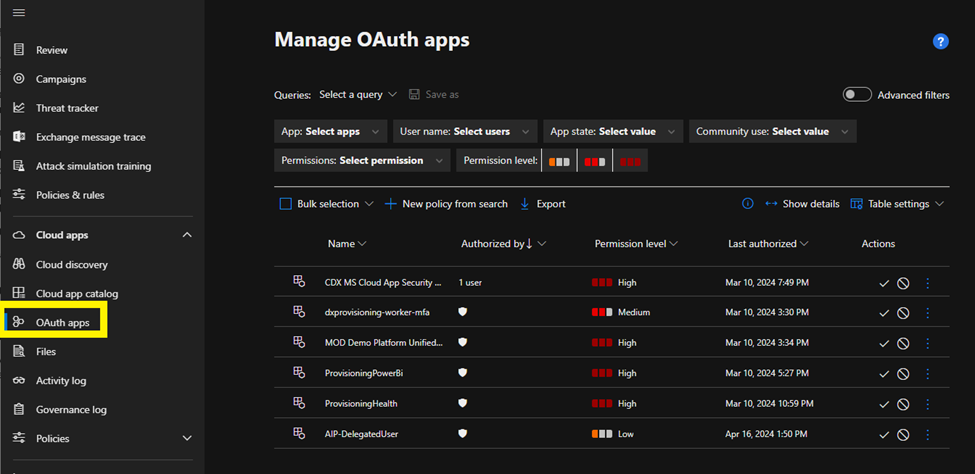
- Discover OAuth apps that have access to your environment:
With OAuth apps users grant cloud apps access to their corporate user accounts without sharing credentials.
To access the OAuth tab:
In the Microsoft Defender Portal, under Cloud Apps select OAuth apps.
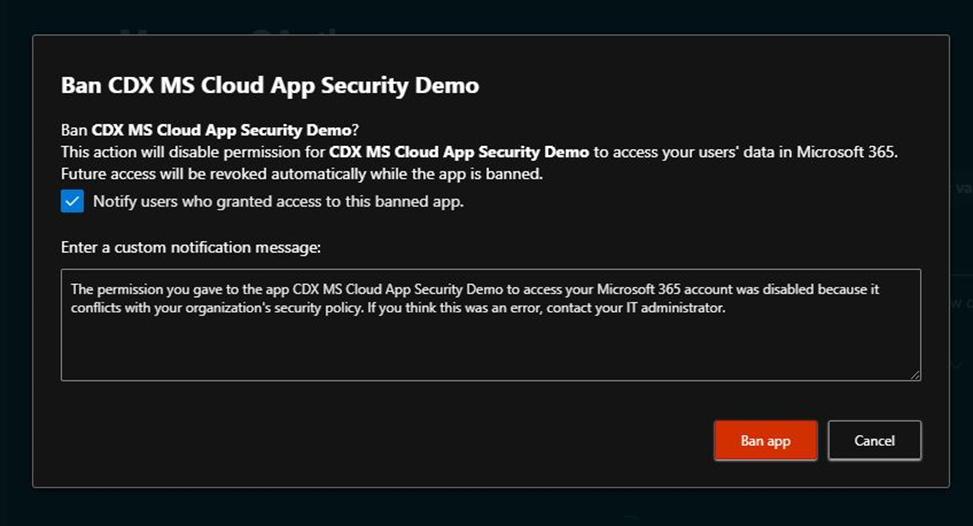
To ban the app, select the ban icon at the end of the app row in the table.
Ban or approve an app:
To ban app icon. You can choose if you want to tell users the app they installed and authorized has been banned. The notification lets users know the app will be disabled and they won’t have access to the connected app. If you don’t want them to know, unselect Notify users who granted access to this banned app in the dialog.
- It’s recommended that you let the app users know their app is about to be banned from use.
To approve the app, select the approve icon at the end of the row in the table. The icon turns green, and the app is approved for all your connected app users.
- When you mark an app as approved, there’s no effect on the end user. This color change is meant to help you see the apps that you’ve approved to separate them from ones that you haven’t reviewed yet.
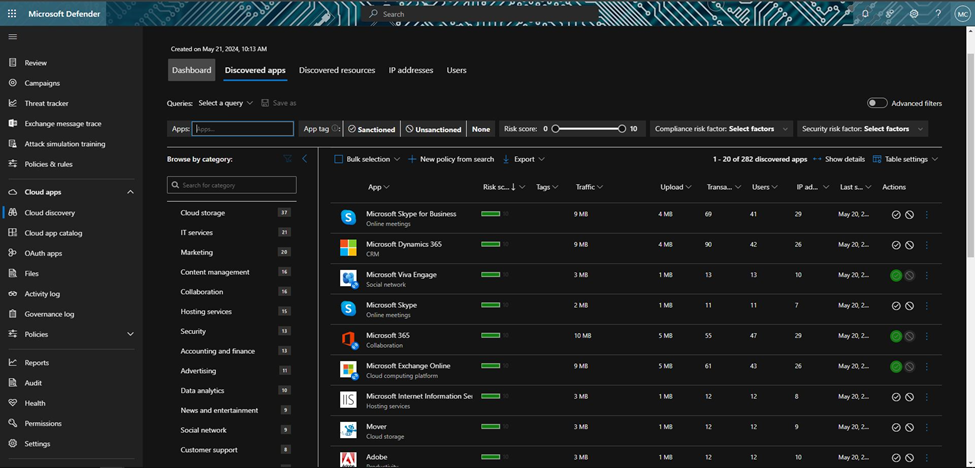
II. Discover and manage shadow IT:
- Analyze Data:
Cloud Discovery Dashboard: Navigate to the Cloud Discovery dashboard in Microsoft Defender for Cloud Apps. This dashboard provides insights into the apps and services being accessed within your organization.
App Tags and Scores: Review the risk scores and tags assigned to discovered apps based on their compliance, security, and business readiness.
2. Identify Risky Apps:
Filter and Search: Use filters to identify high-risk applications based on criteria such as app category, risk score, or user activity.
Review Details: Drill down into individual app details to understand the usage patterns, associated risks, and user activities.
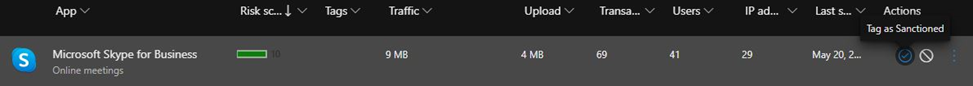
3. Sanction and Unsanctioned Apps:
Mark as Sanctioned or Unsanctioned: Use the Cloud Discovery dashboard to mark discovered apps as sanctioned (approved) or unsanctioned (not approved). This helps in creating policies for managing these apps.
III. Find your cloud app and calculate risk scores:
Cloud app catalog page provides a full list of over 31,000 discoverable cloud apps. Defender for Cloud Apps discovery analyzes your traffic logs against discoverable cloud apps to give your ongoing visibility into cloud use, Shadow IT, and risks posed to your organization. Use the Cloud apps catalog to identify the apps that fit into your organization’s security requirements.
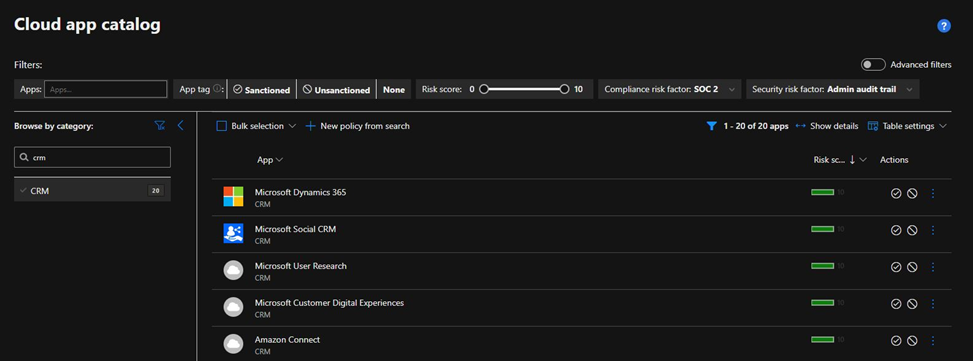
Confirm cloud app security risk
For example, you might want to periodically check that CRM apps used in your organization are adequately secure. In this case, you’d use the following steps to identify your apps:
Sign into Microsoft Defender XDR and select Cloud apps > Cloud app catalog.
In the Browse by category list, select CRM. Use the search box to find a category if needed.
Select the Advanced filters toggle to configure the following advanced filter:
- Compliance risk factor > SOC 2 > equals > Yes
- Compliance risk factor > ISO 27001 > equals > Yes
- Security risk factor > Data-at-rest-encryption method > does not equal > Not supported, NA
- Security risk factor > Admin audit trail > equals > Yes
- Security risk factor > User audit trail > equals > Yes
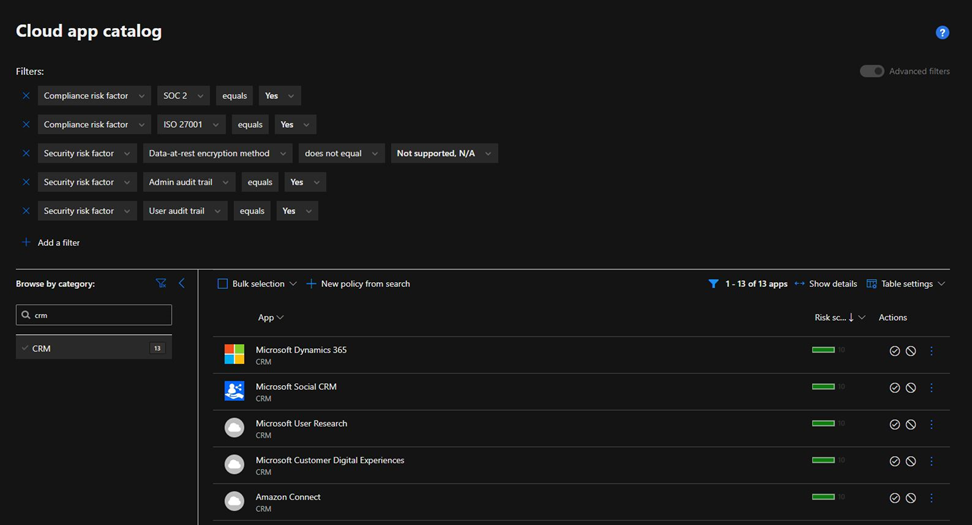
Customize the risk score
By default, all the various parameters evaluated are given equal weight. If there are certain parameters that are more or less important to your organization, it’s important to change them as needed.
For example:
- Sign into Microsoft Defender XDR and select Settings > Cloud Apps > Cloud Discovery > Score metrics.
- For each field or risk category slide the Importance slide to change the weight of the field or the risk category. Importance can be set to Ignored, Low, Medium, High, or Very High.
- Select the N/A values checkbox to define whether a value is either not available or not applicable in the score calculation. When included, N/A values have a negative contribution to the calculated score.
IV. Anomaly detection policies in Defender for Cloud Apps:
Anomaly detection policies in Microsoft Defender for Cloud Apps are designed to identify unusual or suspicious activities that might indicate security threats, such as compromised accounts, insider threats, or malicious activities. These policies leverage machine learning and behavior analytics to detect anomalies based on deviations from typical user behavior. Here’s how to work with anomaly detection policies in Microsoft Defender for Cloud Apps:
Setting Up Anomaly Detection Policies
- Navigate to Policy Management:
- Go to the Microsoft 365 Defender portal.
- Select Cloud Apps under the Policies section to access the Cloud App Security portal.
- In the portal, go to Control and then Policies.
- Create Anomaly Detection Policies:
- Built-in Policies: Microsoft Defender for Cloud Apps provides a set of built-in anomaly detection policies. These include policies for detecting unusual administrative activity, multiple failed login attempts, impossible travel, activity from risky IP addresses, and more.
- Custom Policies: You can also create custom anomaly detection policies tailored to your organization’s specific needs.
- Review and Customize Policies:
- Policy Templates: Use the available templates to create new policies. You can customize parameters like sensitivity levels, activity filters, and thresholds.
- Configuration: Define the scope of the policy by selecting the users or groups to be monitored, the types of activities to track, and the risk levels.
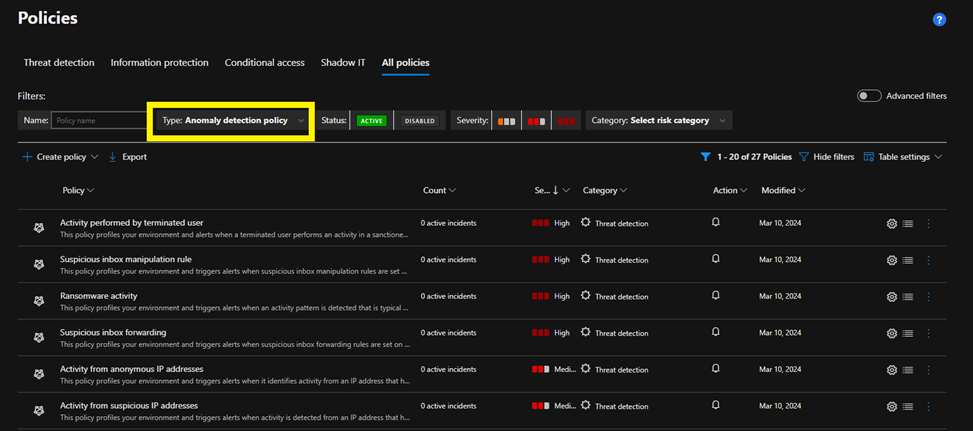
Key Anomaly Detection Policies
Here are some of the key built-in anomaly detection policies available in Microsoft Defender for Cloud Apps:
- Impossible Travel:
- Detects instances where a single user logs in from geographically distant locations within a time frame that would be impossible for a typical travel scenario.
- Suspicious Inbox Forwarding:
- Identifies rules that forward incoming emails to external addresses, which could indicate account compromise.
- Multiple Failed User Logins:
- Triggers alerts for multiple failed login attempts within a specified time period, suggesting a possible brute-force attack.
V. Microsoft Defender for Cloud Apps conditional access app control
Microsoft Defender for Cloud Apps Conditional Access App Control is a security feature that enhances the protection of cloud applications by enabling conditional access policies. This feature integrates with Azure Active Directory (Azure AD) Conditional Access to provide real-time monitoring and control over cloud apps, ensuring that access to corporate resources is governed by specific conditions and policies.
For example:
Use access policies to:
- Block access to Salesforce for users coming from unmanaged devices
- Block access to Dropbox for native clients.
Use session policies to:
- Block downloads of sensitive files from OneDrive to unmanaged devices
Block uploads of malware files to SharePoint Online

Conclusion
CASBs play a vital role in securing cloud environments by providing visibility, control, and compliance capabilities. Organizations can leverage CASBs to mitigate risks, protect data, and ensure a secure cloud adoption strategy. As cloud adoption continues to grow, CASBs will remain essential in the modern cybersecurity landscape.
Mostafa Ashraf
System Engineer
