Welcome to Part two of Deploying Defender External Attack Surface Management.
In the previous post we talked about what is External Attack Surface Management and how it discovers assests with various methods of discovering. In this post we will dig deep on discovering assets and we will look into dashboard.
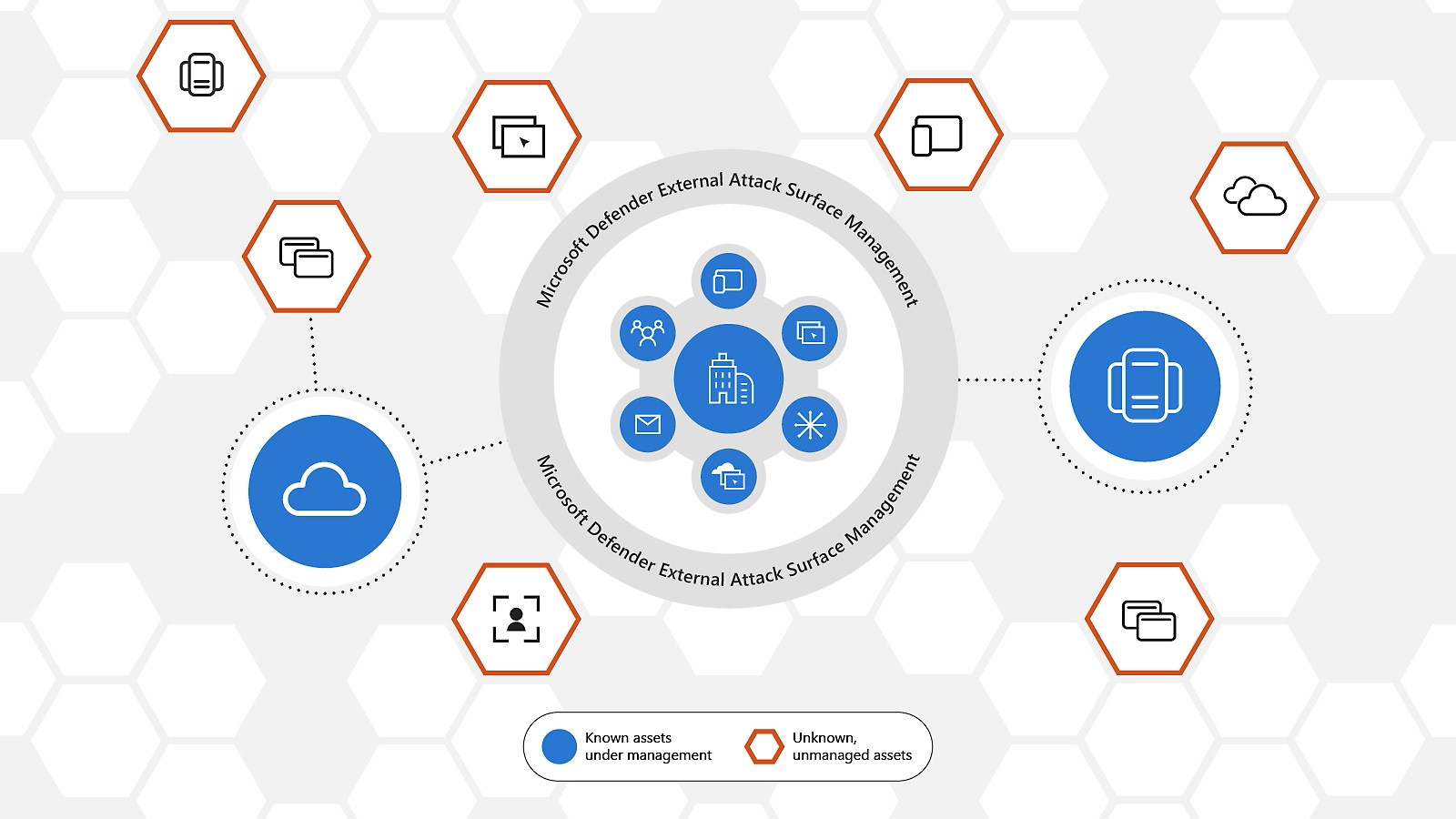
Microsoft Defender External Attack Surface Management (Defender EASM) relies on proprietary discovery technology that scans and discover your organization’s attack surface. Microsoft has preemptively configured the attack surfaces of many organizations, mapping their initial attack surface by discovering infrastructure that’s connected to known assets.
You should check first for your organization’s attack surface before you create any custom attack surface and run other discoveries.
Custom discoveries are organized into discovery groups. They’re independent seed clusters that comprise a single discovery run and operate on their own recurrence schedules. You organize your discovery groups to delineate assets in whatever way best benefits your company and workflows. Common options include organizing by the responsible team or business unit, brands, or subsidiaries.
Create a discovery group
- On the leftmost pane, under Manage, select Discovery.
- The Discovery page shows your list of discovery groups by default. This list is empty when you first access the platform. To run your first discovery, select Add Discovery Group.
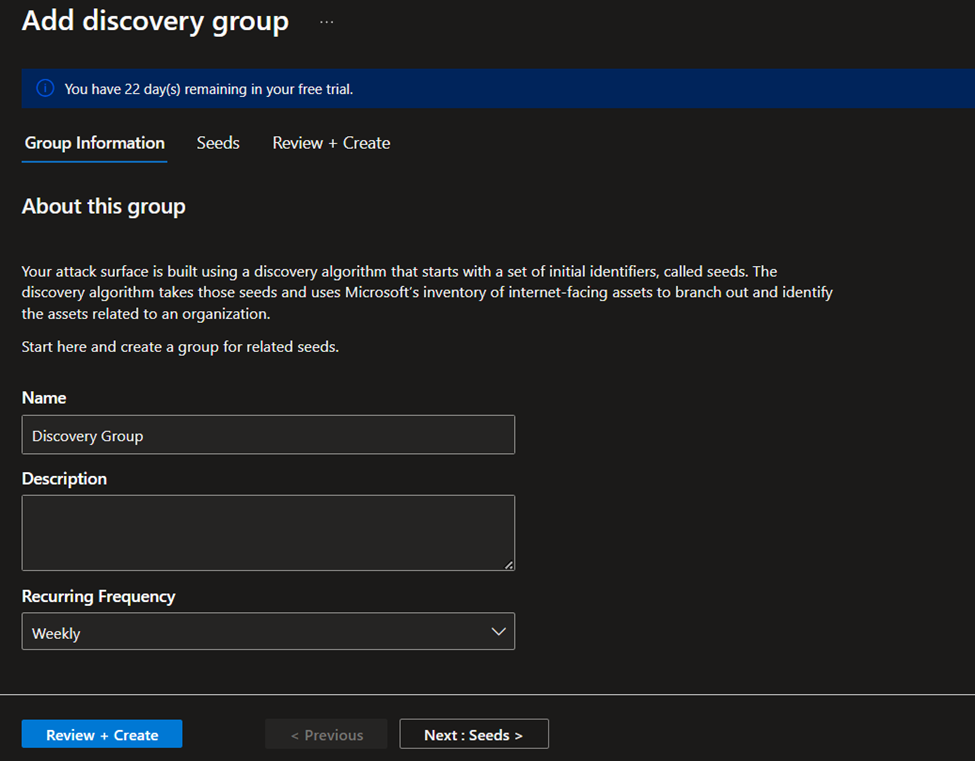
Name your new discovery group and add a description. The Recurring Frequency field allows you to schedule discovery runs for this group by scanning for new assets related to the designated seeds on a continuous basis. The default recurrence selection is Weekly.
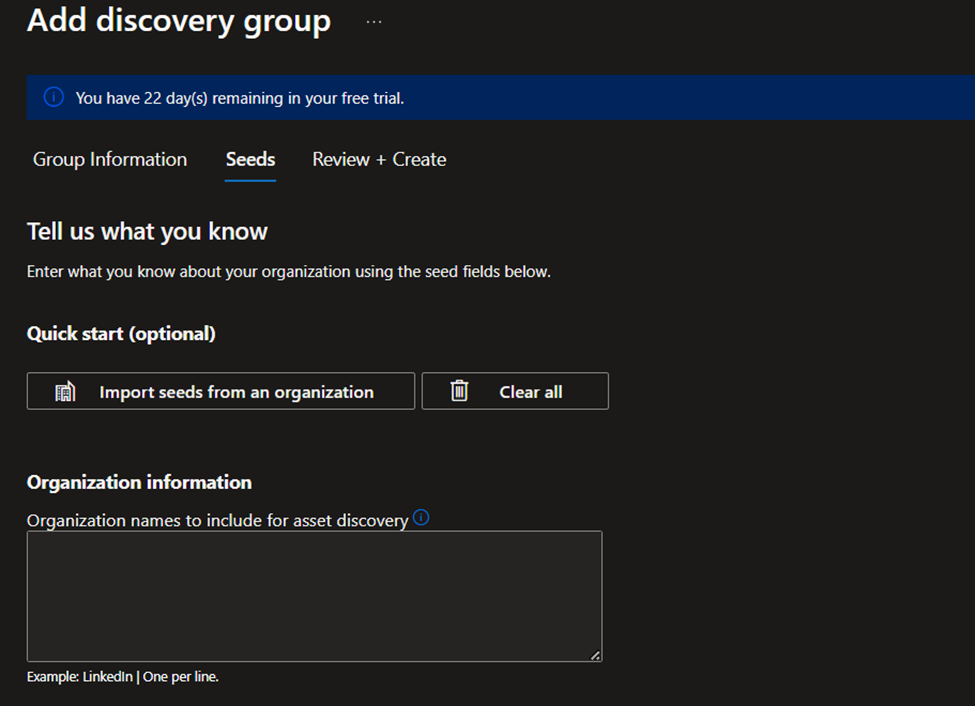
The Quick Start option lets you search for your organization in a list of prepopulated attack surfaces. You can quickly create a discovery group based on the known assets that belong to your organization.
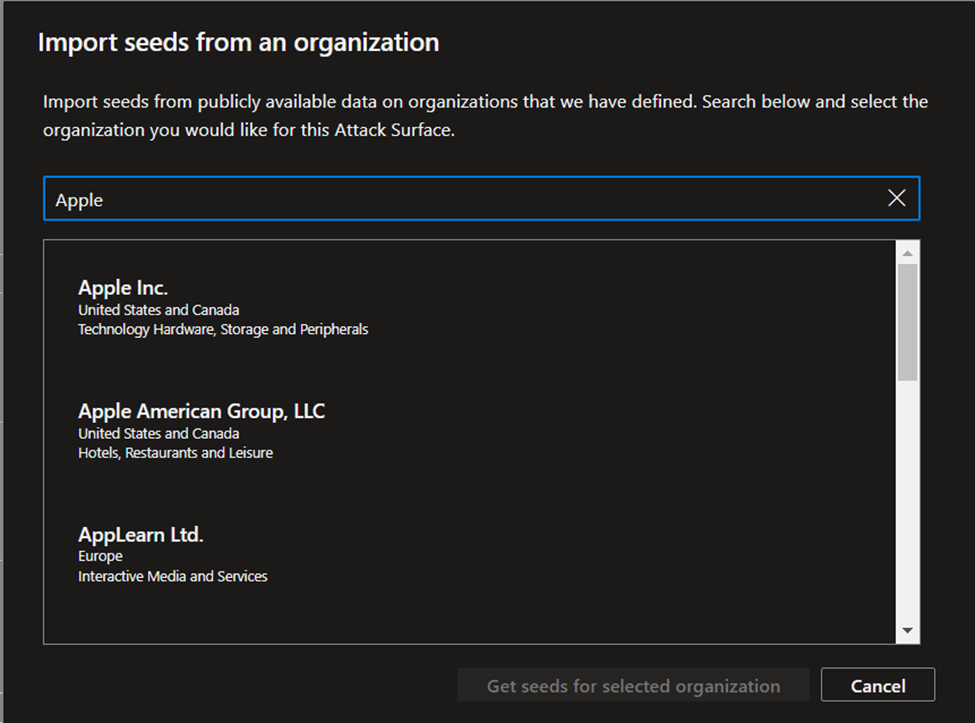
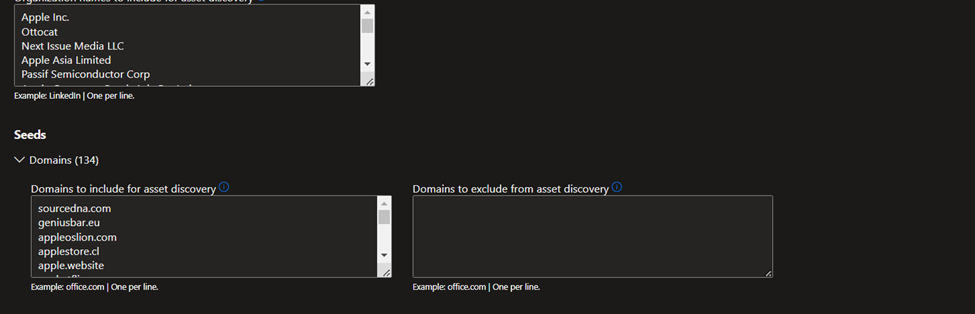
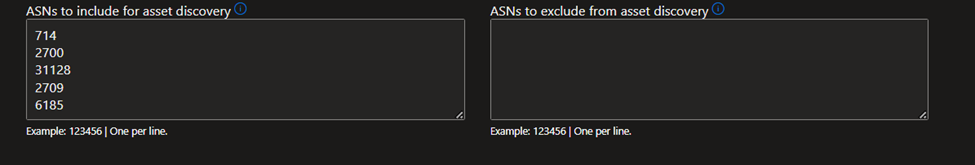
Alternatively, you can manually input your seeds. Defender EASM accepts organization names, domains, IP blocks, hosts, email contacts, ASNs, and Whois organizations as seed values.
You can also specify entities to exclude from asset discovery to ensure they aren’t added to your inventory if detected. For example, exclusions are useful for organizations that have subsidiaries that will likely be connected to their central infrastructure, but don’t belong to their organization.
After your seeds are selected, select Review + Create.
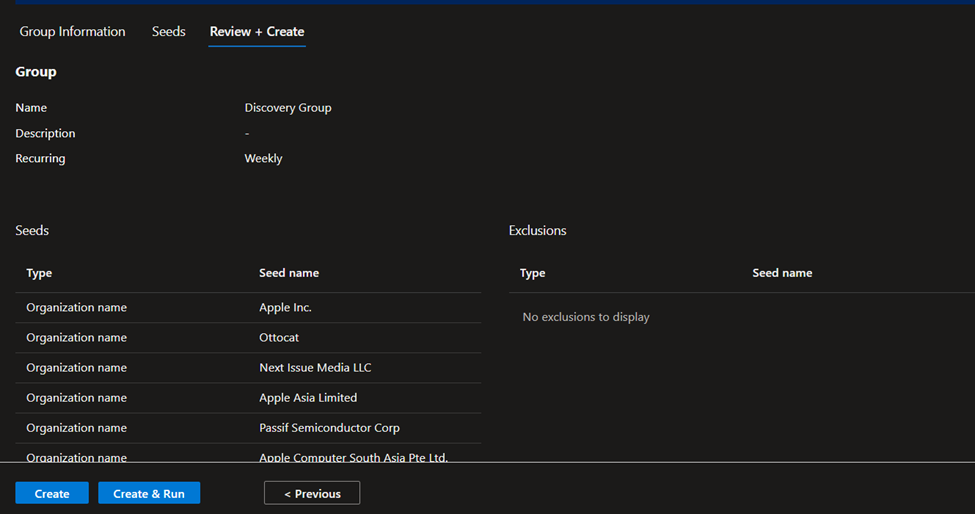
Review your group information and seed list and select Create & Run.
Seeds
The seed list view displays seed values with three columns: Type, Source Name, and Discovery Groups. The Type field displays the category of the seed asset. The most common seeds are domains, hosts, and IP blocks. You can also use email contacts, ASNs, certificate common names, or Whois organizations.
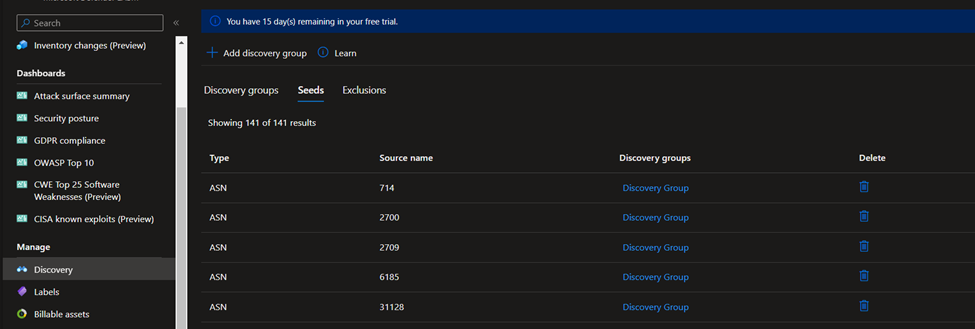
Exclusions
Similarly, you can select the Exclusions tab to see a list of entities that were excluded from the discovery group. These assets won’t be used as discovery seeds or be added to your inventory. Exclusions only affect future discovery runs for an individual discovery group.
Dashboards
Defender EASM has six types of dashboards. These dashboards help you understand your environment and your discovered assets.
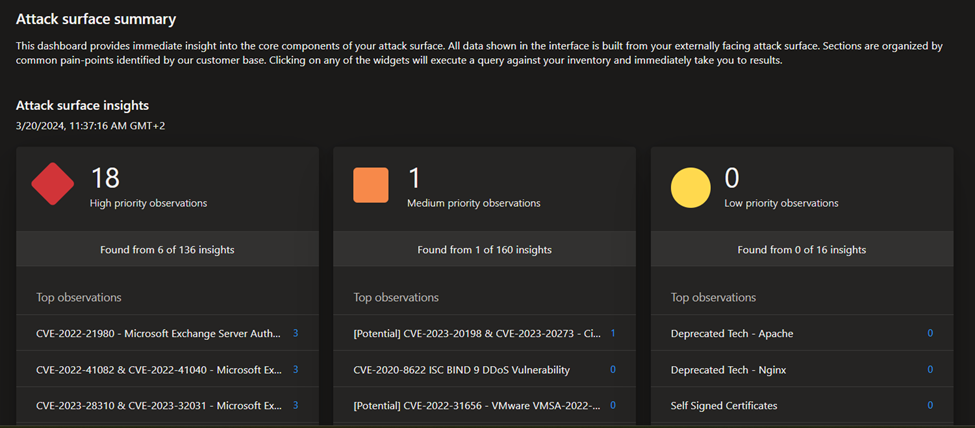
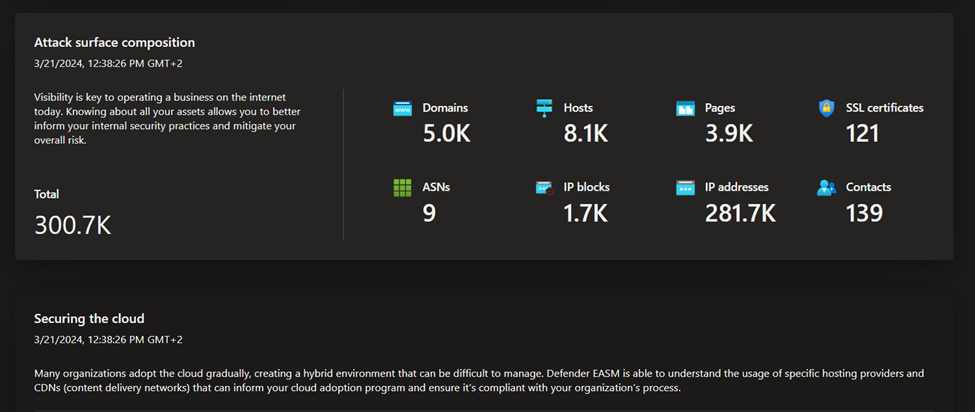
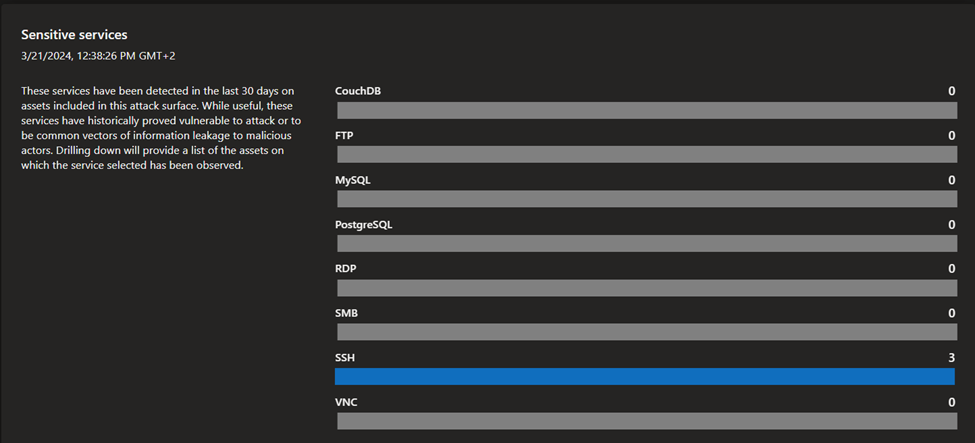
- Attack surface summary: this dashboard summarizes the key observations derived from your inventory. It provides a high-level overview of your Attack Surface and the asset types that comprise it, and surfaces potential vulnerabilities by severity (high, medium, low). This dashboard also provides key context on the infrastructure that comprises your Attack Surface. This context includes insight into cloud hosting, sensitive services, SSL certificate and domain expiry, and IP reputation.
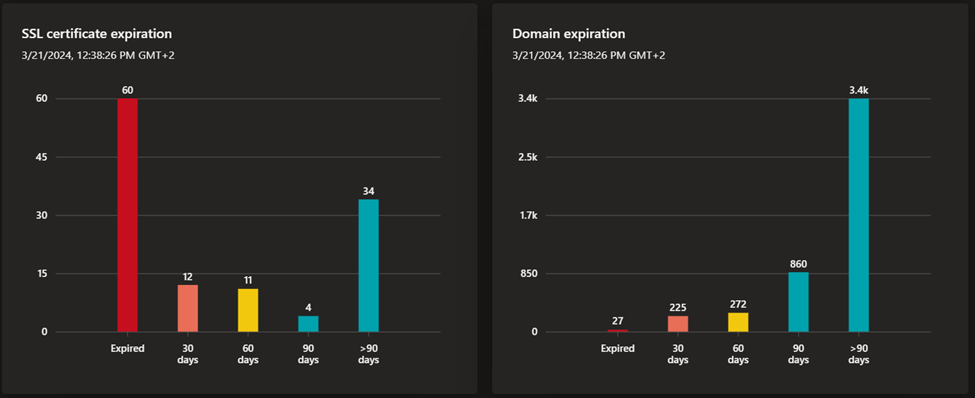
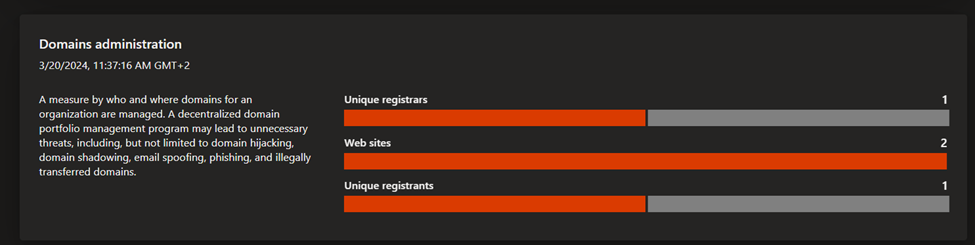
- Security posture: this dashboard helps organizations understand the maturity and complexity of their security program based on the metadata derived from assets in your Approved inventory. It is comprised of technical and nontechnical policies, processes and controls that mitigate risk of external threats. This dashboard provides insight on CVE exposure, domain administration and configuration, hosting and networking, open ports, and SSL certificate configuration.
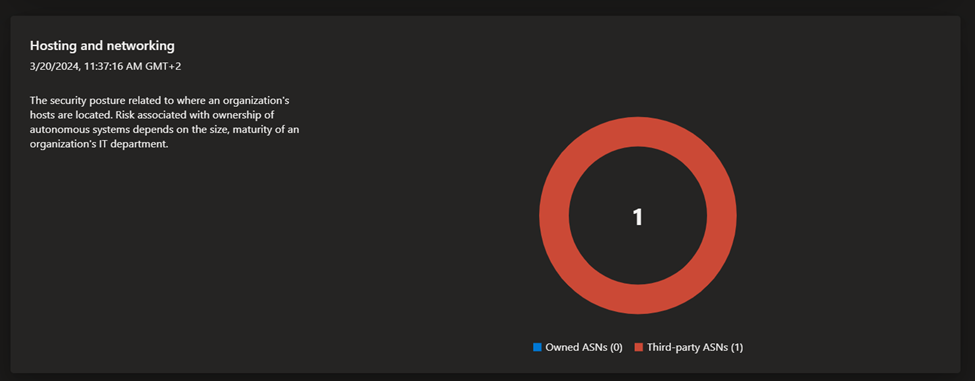
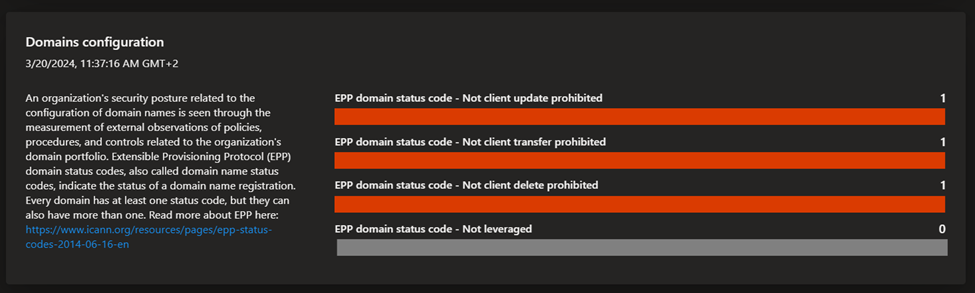
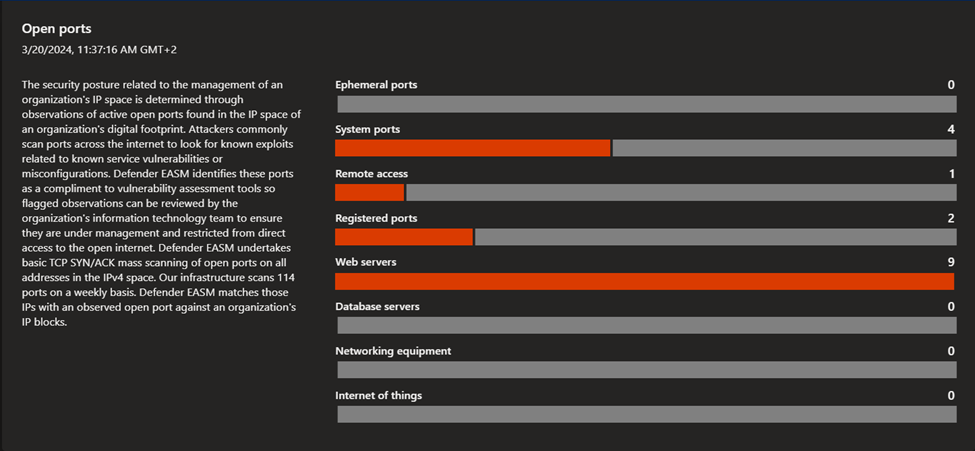
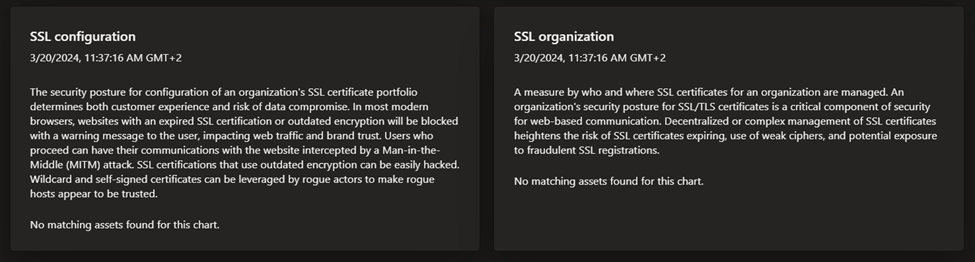
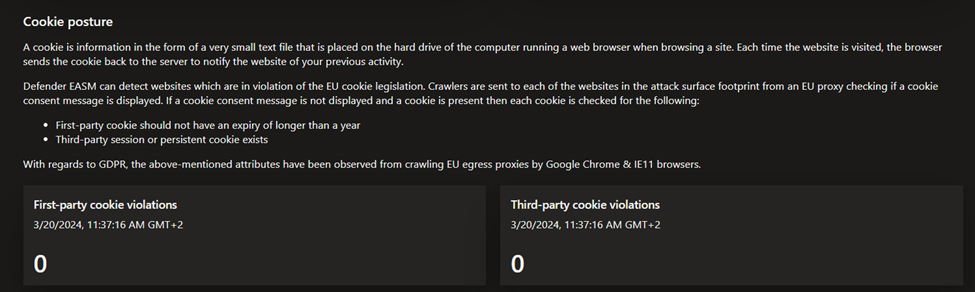
- GDPR compliance: this dashboard surfaces key areas of compliance risk based on the General Data Protection Regulation (GDPR) requirements for online infrastructure that’s accessible to European nations. This dashboard provides insight on the status of your websites, SSL certificate issues, exposed personal identifiable information (PII), login protocols, and cookie compliance.
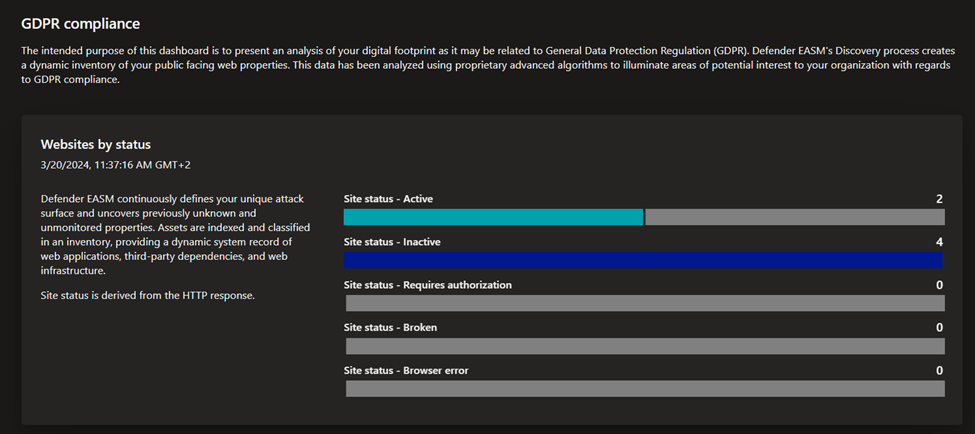
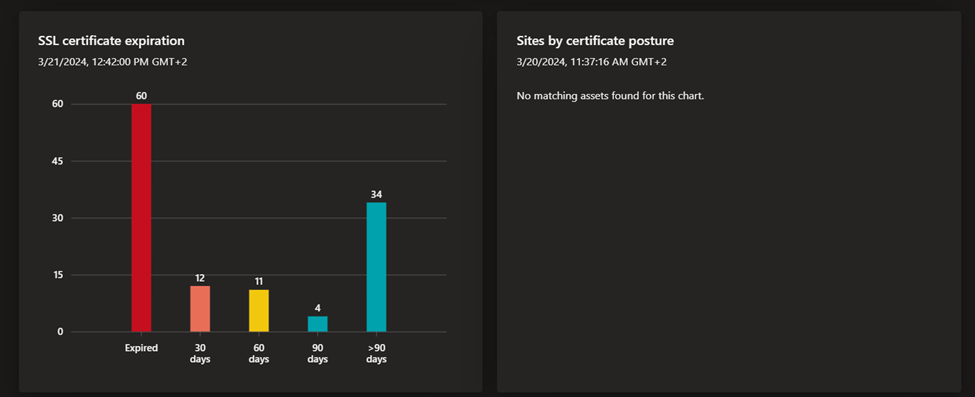
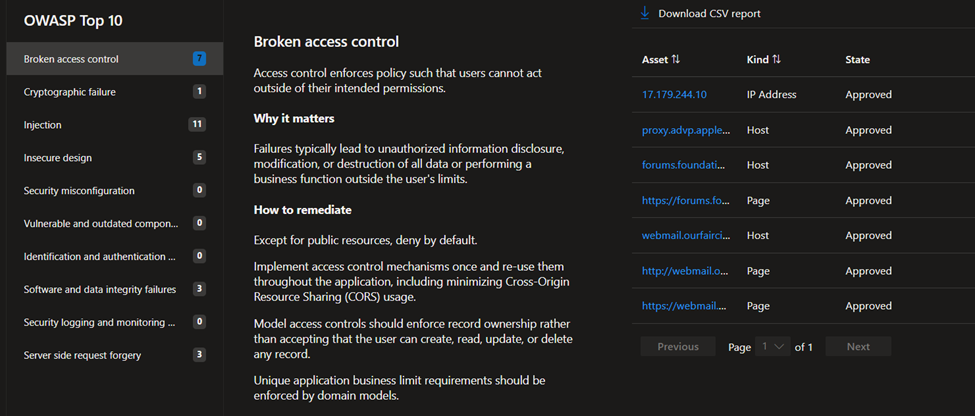
- OWASP Top 10: this dashboard surfaces any assets that are vulnerable according to OWASP’s list of the most critical web application security risks. On this dashboard, organizations can quickly identify assets with broken access control, cryptographic failures, injections, insecure designs, security misconfigurations and other critical risks as defined by OWASP.
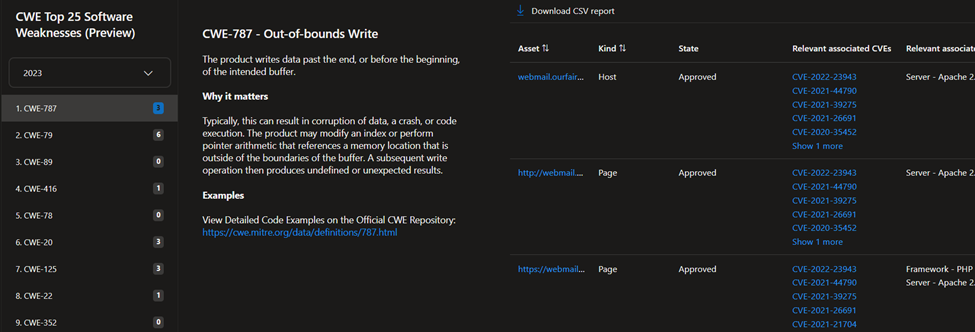
- CWE top 25 software weaknesses: this dashboard is based on the Top 25 Common Weakness Enumeration (CWE) list provided annually by MITRE. These CWEs represent the most common and impactful software weaknesses that are easy to find and exploit.
- CISA known exploits: this dashboard displays any assets that are potentially impacted by vulnerabilities that led to known exploits as defined by CISA. This dashboard helps you prioritize remediation efforts based on vulnerabilities that were exploited in the past, indicating a higher level of risk for your organization.
Conclusion
The new Microsoft Defender External Attack Surface Management tool is really interesting and can be used for various reasons to prevent the unknown and get more valuable insights into the online internet-exposed posture.
I hope this was informative for you, please let me know your comments.
See you soon
Karim Hamdy
Infrastructure Architect