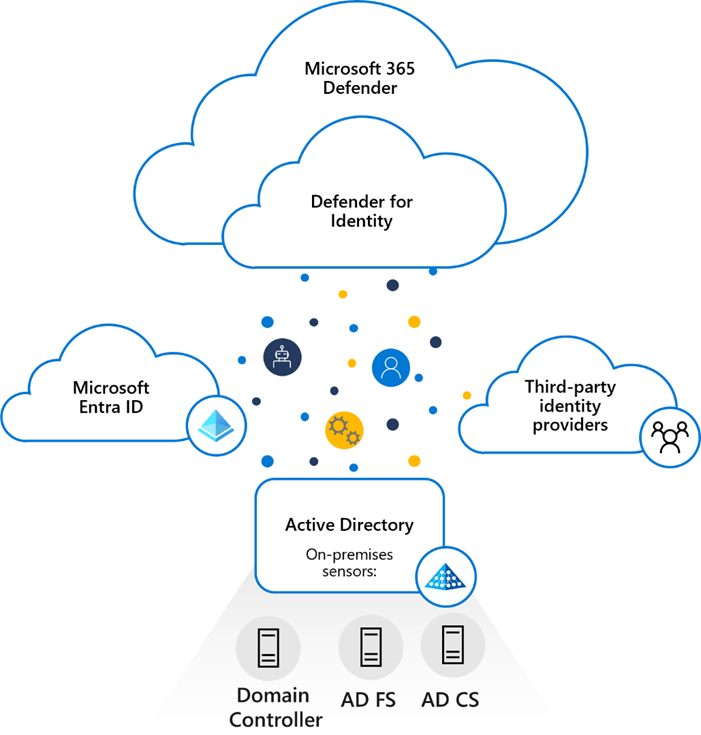
In the previous post we talked about Zero Trust Architecture and it’s six pillars. Microsoft Defender for Identity stands out as a powerful tool designed to protect on-premises Active Directory (AD) environments while seamlessly integrating with cloud-based Azure Active Directory (Azure AD).
Whether you’re defending against credential theft, lateral movement, or advanced persistent threats, Defender for Identity provides the visibility and tools you need to detect, investigate, and respond to identity-related risks effectively.
What is Microsoft Defender for Identity?
Microsoft Defender for Identity (formerly Azure Advanced Threat Protection or Azure ATP) is a cloud-based security solution that uses your on-premises Active Directory signals to detect, analyze, and respond to advanced threats. It enriches these insights with Microsoft’s global threat intelligence, providing robust protection against identity-focused attacks.
Key Features:
- Threat Detection: Spot malicious activities like brute-force attacks, pass-the-hash, and Kerberos golden ticket exploits.
- Compromised Account Detection: Identify potentially compromised accounts and insider threats.
- Lateral Movement Path (LMP) Analysis: Expose potential attack paths to high-value assets within your network.
- Seamless Integration with Microsoft Security Stack: Works alongside tools like Microsoft Sentinel, Microsoft Defender for Endpoint, and Entra ID Identity Protection.
Why Defender for Identity is Crucial in Hybrid Scenarios
Hybrid environments, which combine on-premises and cloud systems, are particularly susceptible to identity-based attacks. Attackers often exploit vulnerabilities in on-premises Active Directory to gain access to cloud resources.
Defender for Identity ensures comprehensive protection by monitoring:
- Domain controllers for suspicious activities.
- Identity traffic for anomalies, such as unauthorized lateral movement or privilege escalation.
- Account activity for patterns indicative of compromise.
This capability is essential for organizations transitioning to hybrid or cloud environments, as it bridges the gap between legacy systems and modern identity solutions.
How It Works
- Data Collection: Lightweight sensors installed on domain controllers capture real-time signals, such as logins and authentication events.
- Analysis: The cloud-based service analyzes signals using AI and behavioral analytics to detect anomalies.
- Alerting: Security incidents are flagged in the Microsoft 365 Defender portal with actionable insights for remediation.
- Response: Integrates with tools like Microsoft Sentinel to enable automated threat hunting and response.
Installed directly on your domain controller, Active Directory Federation Services (AD FS), or Active Directory Certificate Services (AD CS) servers, the Defender for Identity sensor accesses the event logs it requires directly from the servers. After the logs and network traffic are parsed by the sensor, Defender for Identity sends only the parsed information to the Defender for Identity cloud service.
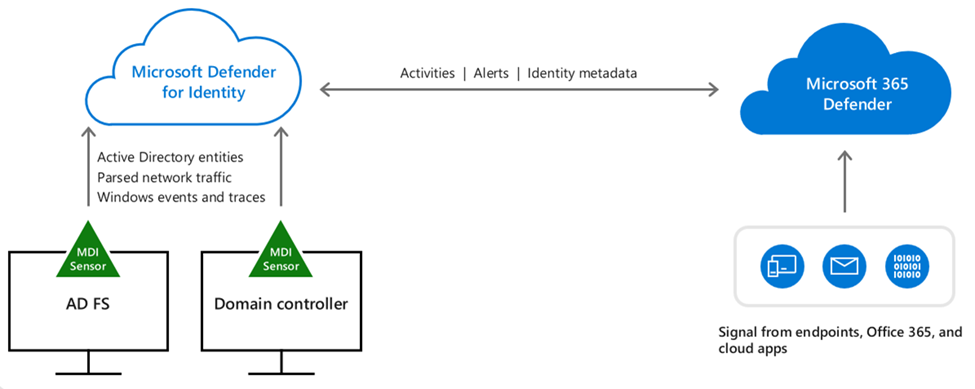
The Defender for Identity sensor has the following core functionality:
- Capture and inspect domain controller network traffic (local traffic of the domain controller)
- Receive Windows Events directly from the domain controllers
- Receive RADIUS accounting information from your VPN provider
- Retrieve data about users and computers from the Active Directory domain
- Perform resolution of network entities (users, groups, and computers)
- Transfer relevant data to the Defender for Identity cloud service
Microsoft Defender for Identity categorizes its security alerts into distinct categories to help organizations understand and respond effectively to various types of threats. These categories group alerts by the nature of the suspicious activity, providing clear context and prioritization.
1. Reconnaissance
- Description: Alerts related to activities where attackers attempt to gather information about the environment before launching an attack.
- Examples:
- LDAP enumeration of sensitive accounts or groups.
- Account enumeration via Kerberos (e.g., Kerberoasting).
- SMB session enumeration.
2. Credential Compromise
- Description: Indicates attempts to steal or misuse credentials to gain unauthorized access.
- Examples:
- Pass-the-Hash attacks.
- Pass-the-Ticket attacks.
- Kerberos golden or silver ticket activities.
- Brute-force or password spray attacks.
3. Lateral Movement
- Description: Alerts about activities indicating attempts to move laterally across systems within the network to gain access to additional resources.
- Examples:
- Use of tools like PsExec, WMI, or remote desktop for lateral movement.
- Malicious use of stolen credentials to access additional systems.
- Detection of abnormal resource access patterns.
4. Privilege Escalation
- Description: Flags attempts to elevate permissions to gain administrative or sensitive access.
- Examples:
- Unusual access by a sensitive account.
- Attempts to modify domain administrator privileges.
- DCShadow or unauthorized replication of Active Directory data.
5. Sensitive Account Activities
- Description: Focuses on unusual or unauthorized use of accounts with elevated privileges, such as domain administrators.
- Examples:
- Unusual login locations or times for privileged accounts.
- Suspicious changes in account configurations.
- Use of sensitive accounts for anomalous activities.
Defender for Identity is a vital part of Microsoft’s Zero Trust security strategy, focusing on continuous validation and least-privilege access. In our next post, we’ll walk you through a practical demo to showcase Defender for Identity’s capabilities in action. Stay tuned!
Have questions or want to share your experience with Defender for Identity? Drop a comment below!
See you soon
Karim Hamdy
Infrastructure Architect