The Challenge
You manage a Microsoft 365 E5 environment where employees access sensitive data daily — Outlook, SharePoint, Teams, and internal SaaS tools.
Your goal:
Ensure that users can only access resources in your environment from a device that has the Global Secure Access (GSA) client connected.
The reason is simple — traditional Conditional Access rules can control who signs in and what device they use, but not necessarily how that traffic reaches Microsoft 365.
Without network-level enforcement, even a stolen session token could be replayed from an attacker’s system outside your corporate environment.
That’s where Microsoft Entra Global Secure Access signaling comes in.
🌐 The Concept
Global Secure Access signaling allows Microsoft Entra ID (formerly Azure AD) to detect whether a user’s traffic is flowing through your organization’s Global Secure Access network — i.e., whether they’re connected via the GSA client.
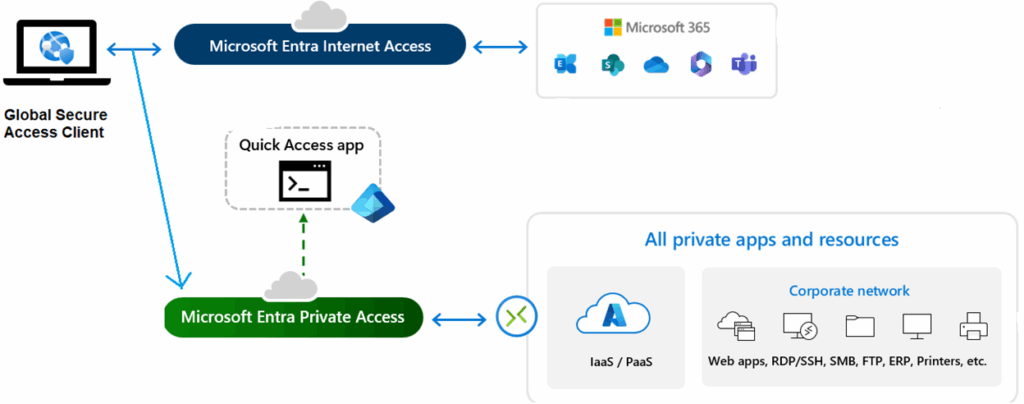
When enabled, Entra Conditional Access receives a “signal” identifying traffic as compliant (coming through your secure tunnel).
You can then build a Conditional Access policy that blocks any user not connected via the GSA client.
In short:
- Connected through GSA client? ✅ Access granted
- Bypassing GSA client? ❌ Access denied
It’s a direct, policy-driven way to enforce that all access to Microsoft 365 apps happens through a trusted and monitored network path.
🧠 Why This Matters — The Benefits
1. 🛡️ Protection Against Token Theft
Even if an attacker steals a user’s session token, it’s useless outside your compliant network.
Because Conditional Access validates the network signal, any replayed session from outside GSA is automatically blocked.
2. 🔐 True Zero Trust Enforcement
Global Secure Access signaling connects the network layer and identity layer, enforcing the principle of “never trust, always verify.”
It ensures that identity-based access decisions also consider where and how the session originates.
3. 💼 VPN-Free Secure Access
Users connect to Microsoft 365 or SaaS apps through the lightweight GSA client — no VPN setup, no manual network configuration.
This creates a secure, consistent access experience from any device, anywhere.
4. 📊 Improved Visibility and Auditing
All access attempts are logged with network compliance information.
Security teams can easily see whether access was compliant, and where policy enforcement blocked unsafe connections.
5. ⚙️ Simplified Conditional Access Policies
Instead of managing dozens of IP ranges or VPN addresses, admins can simply use the built-in “All Compliant Network Locations” condition to identify GSA traffic — reducing policy complexity.
⚙️ How It Works (Simplified)
- A user signs in from a device with the Global Secure Access client active.
- Traffic is routed through Microsoft’s secure network and associated with your GSA tenant.
- Entra ID receives a signaling header that marks the traffic as coming from a compliant network.
- Your Conditional Access policy checks for this signal before granting access.
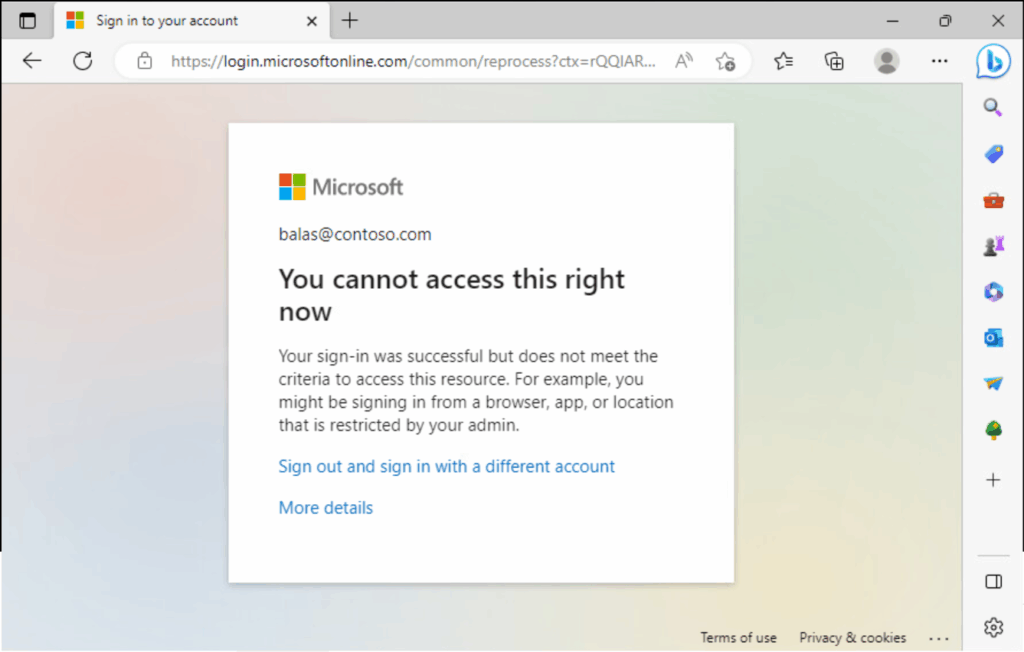
- If the client is disconnected, the signal isn’t present — and access is blocked.
🪜 Enabling It (High-Level Steps)
- In Microsoft Entra Admin Center, go to:
Global Secure Access → Settings → Session Management → Adaptive Access. - Toggle on “Enable CA signaling for Entra ID (covering all cloud apps).”
- Confirm the system-created “All Compliant Network locations” entry under Conditional Access → Named Locations.
- Create a Conditional Access policy that blocks access unless the connection is from this compliant network.
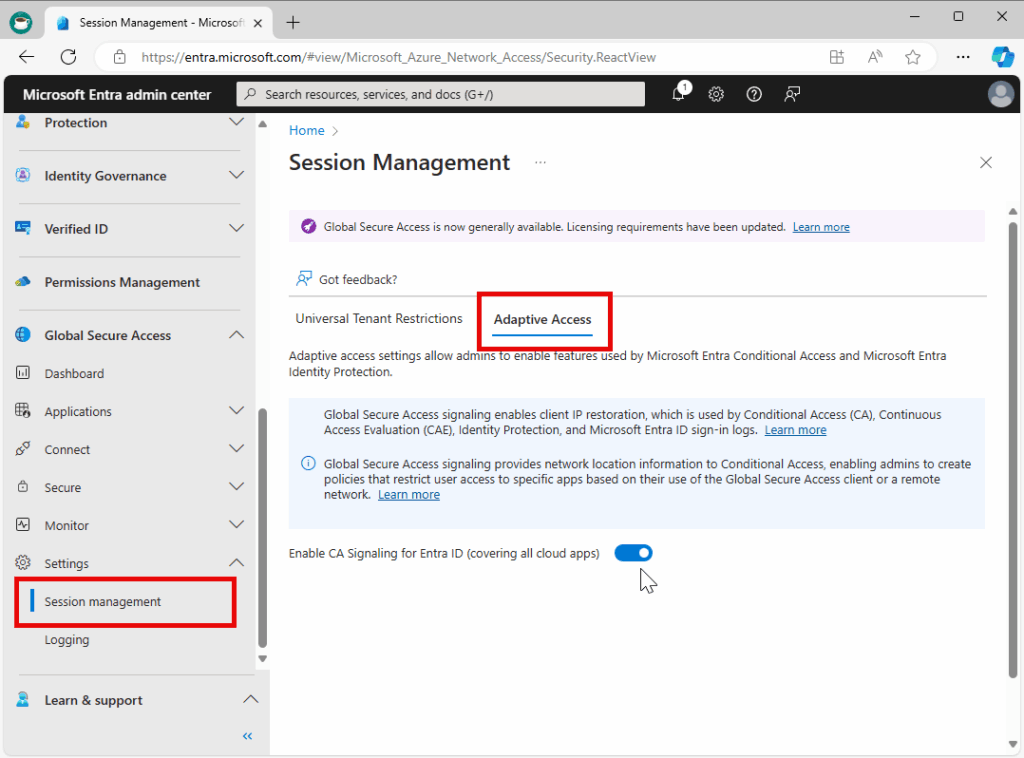
Once this is in place, all users must be connected to the GSA client to reach your Microsoft 365 and SaaS resources — achieving true network compliance.
Summary
Enabling Global Secure Access signaling transforms Conditional Access from being purely identity-based to identity + network aware.
It’s a small configuration change with major security benefits:
✅ Prevents token theft and replay attacks
✅ Enforces zero trust network access
✅ Simplifies policy management
✅ Improves auditing and reporting
✅ Delivers a seamless, VPN-free user experience
By requiring all traffic to route through the Global Secure Access client, you close the gap between authentication and network trust — ensuring that every connection to your Microsoft 365 environment is secure, verified, and compliant.
I hope this has been informative for you.
See you soon
Karim Hamdy
Infrastructure Architect
