A Zero Trust strategy empowers you to navigate modern security challenges with confidence. The Zero Trust Architecture is an approach to modern security, designed to address the evolving threat landscape by assuming that breaches are inevitable or have already occurred. This model emphasizes verification, least-privilege access, and comprehensive monitoring to protect users, devices, applications, and data—whether on-premises or in the cloud.
Core Principles of Zero Trust Approach
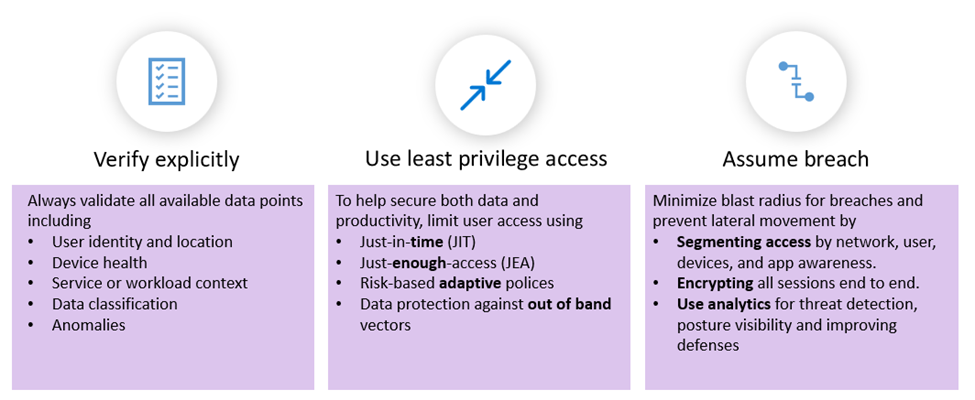
- Verify Explicitly:
Always authenticate and authorize based on all available data points, such as user identity, location, device health, service or workload, and data classification. - Use Least-Privilege Access:
Minimize access to resources and limit user permissions to only what is necessary, using Just-In-Time (JIT) and Just-Enough-Access (JEA) principles. - Assume Breach:
Operate as if every network and endpoint is already compromised. Leverage threat intelligence, telemetry, and AI to detect, respond, and recover swiftly.
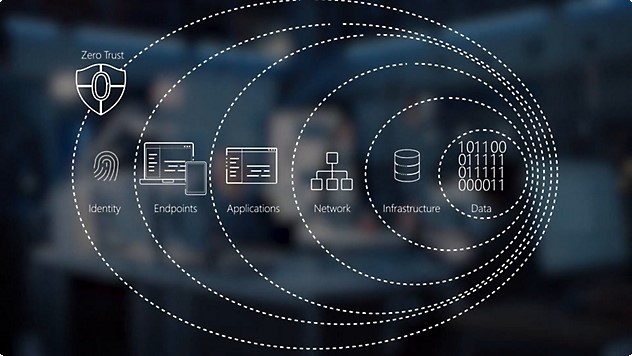
The Zero Trust Architecture is built upon six foundational pillars, each addressing a critical component of modern security. These pillars ensure that all aspects of an organization’s environment adhere to Zero Trust principles: assume breach, verify explicitly, and apply least privilege access. Below is Microsoft’s implementation for ZTA:

Here’s an overview of the six pillars:
1. Identity
- Focus: Secure authentication and authorization of users and devices.
- Key Practices:
- Use Multi-Factor Authentication (MFA).
- Implement Conditional Access Policies.
- Continuously monitor identity signals for anomalies (e.g., risk-based access control).
- Microsoft Tools: Microsoft Entra.
2. Endpoint
- Focus: Ensure all devices accessing resources are healthy and compliant.
- Key Practices:
- Enforce endpoint compliance through device management solutions.
- Use threat protection and antivirus measures.
- Regularly patch and update devices.
- Microsoft Tools: Microsoft Intune, Defender for Endpoint.
3. Network
- Focus: Segment and secure network traffic to prevent unauthorized lateral movement.
- Key Practices:
- Implement micro-segmentation.
- Encrypt internal and external communications (e.g., TLS).
- Monitor and restrict unauthorized traffic.
- Microsoft Tools: Azure Firewall, Azure Virtual Network (VNet), Microsoft Defender for Cloud.
4. Data
- Focus: Protect sensitive information at rest, in transit, and in use.
- Key Practices:
- Classify and label data based on sensitivity.
- Apply encryption and Data Loss Prevention (DLP) policies.
- Continuously monitor for unauthorized access or exfiltration.
- Microsoft Tools: Microsoft Purview, Microsoft Information Protection.
5. Applications
- Focus: Ensure security and compliance across software and services.
- Key Practices:
- Secure access to applications with strong identity controls.
- Employ runtime application protection and API security.
- Monitor for vulnerabilities and enforce patch management.
- Microsoft Tools: Microsoft Defender for Cloud Apps.
6. Infrastructure
- Focus: Secure cloud and on-premises workloads, containers, and resources.
- Key Practices:
- Apply Just-In-Time (JIT) access to infrastructure.
- Continuously monitor for misconfigurations or vulnerabilities.
- Automate threat detection and response.
- Microsoft Tools: Microsoft Defender for Cloud, Azure Policy.
Next time we’ll talk about Microsoft Defender for Identity with a few use cases, so stay tuned!
I hope this was informative for you, please let me know your comments.
See you soon
Karim Hamdy
Infrastructure Architect