Office 365 Conditional Access (CA) is a feature within the Microsoft 365 security suite designed to help organizations enforce specific access controls and policies based on various conditions. These conditions can include user roles, device compliance, locations, applications, and risk levels. Here are some key aspects of Office 365 Conditional Access:
Key Features of Office 365 Conditional Access:
- Policy-Based Access Control:
- Administrators can create policies that define conditions under which access to Office 365 resources is granted or denied
- User and Group-Based Policies:
- Policies can be targeted to specific users or groups within the organization. This allows for differentiated access controls based on user roles or departments.
- Location-Based Controls:
- Access can be restricted based on the geographic location of the user. For example, access can be allowed only from trusted IP addresses or blocked from specific regions.
- Device Compliance:
- Ensure that only devices that meet the organization’s compliance standards such as having the latest updates.
- Application Enforcement:
- Conditional Access policies can be applied to specific Office 365 applications like SharePoint Online, Teams, etc.
- Risk-Based Access:
- Integration with Azure Active Directory Identity Protection allows Conditional Access to respond to risk signals. For example, if a sign-in attempt is detected to be risky, additional verification methods like Multi-Factor Authentication (MFA) can be required.
- Session Controls:
- Granular controls over user sessions can be enforced, such as limiting session duration or requiring re-authentication for sensitive actions.
Implementing Conditional Access:
- Define Policies:
- Start by identifying the scenarios where conditional access is necessary, such as securing access for remote workers and protecting sensitive data.
- Configure Conditions:
- Specify the conditions that must be met for access to be granted. This includes selecting users or groups, defining location-based controls, and setting device compliance requirements.
- Set Access Controls:
- Decide on the controls to enforce when conditions are met. This could include allowing access, requiring MFA, or blocking access entirely.
- Test and Monitor:
- Before enforcing policies broadly, test them with a subset of users to ensure they work as expected.
Use Case:
Scenario: A company that has on-prem AD users and wants to protect its Office 365 environment from unauthorized access while supporting a mobile workforce.
Policy Setup:
- Users: Apply to all employees.
- Conditions:
- Allow access only from managed devices (devices that are enrolled and compliant with Intune policies).
- Require MFA for access from unfamiliar locations or devices.
- Access Controls:
- Require MFA for all sign-ins.
- Grant access only if the device is compliant.
Demo Steps:
- Create Virtual Machines:
- Deploy two virtual machines on-prem one of them a Windows server for DC and another as a Windows Client that will be installed O365 on it
- Create Tenant:
- Deploy a tenant in Microsoft Azure
- Create User’s
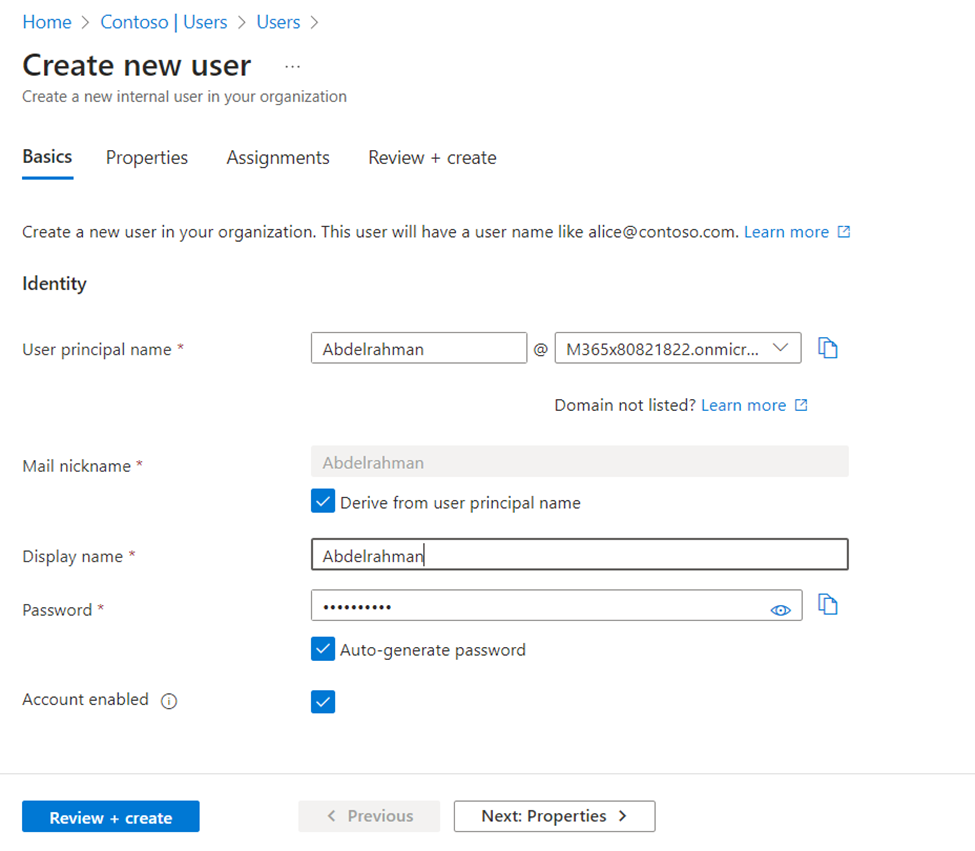
- Create a user from Entra ID
- In the Azure portal, Navigate to Entra ID and Access the “Users” section: then Click on Add a new user
- Create a user from Entra ID
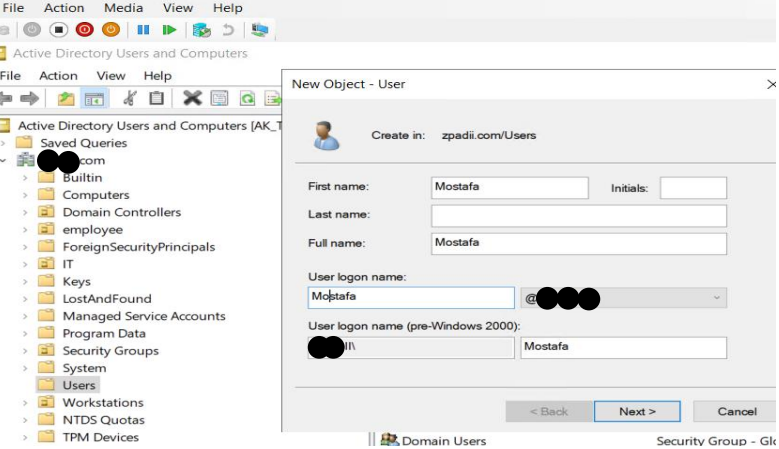
- Create a user from ADDC
- Azure AD Connect
- We will use Azure AD Connect to Synchronize users between ADDC and Entra ID
- implement multi-factor authentication (MFA)
- Multi-factor authentication (MFA) is a security method that requires multiple forms of verification, like a password and a fingerprint scan, to access an account or system. It adds an extra layer of security beyond just a password.
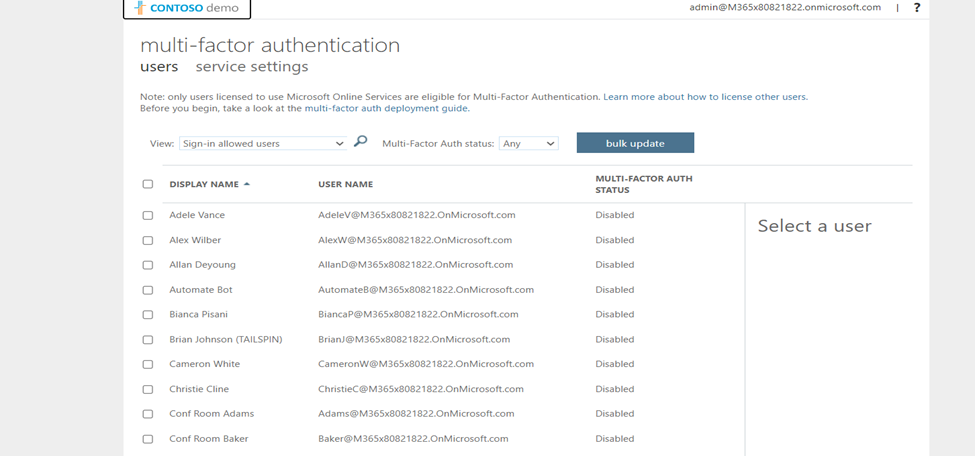
- We can get it from the Azure portal, Navigate to Entra ID Access the “Per-User MFA” section:
- Multi-factor authentication (MFA) is a security method that requires multiple forms of verification, like a password and a fingerprint scan, to access an account or system. It adds an extra layer of security beyond just a password.
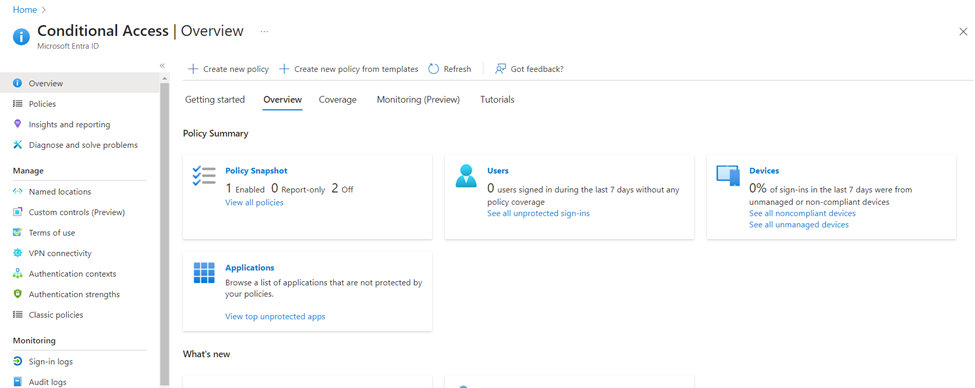
- Conditional Access (CA)
- allows you to control access to Office 365 and other Microsoft apps based on various conditions
- We can get it from the Azure portal, Navigate to Entra ID > Security > Conditional Access
- allows you to control access to Office 365 and other Microsoft apps based on various conditions
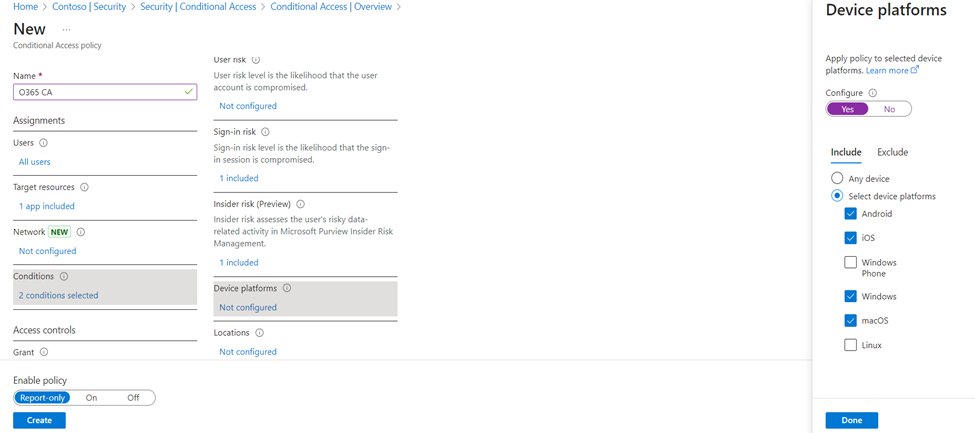
- We will use the Device Platforms conditions that can define specific rules or settings based on the type of device accessing Office 365 services. This can include conditions such as whether the device is running Windows, macOS, iOS, or Android.
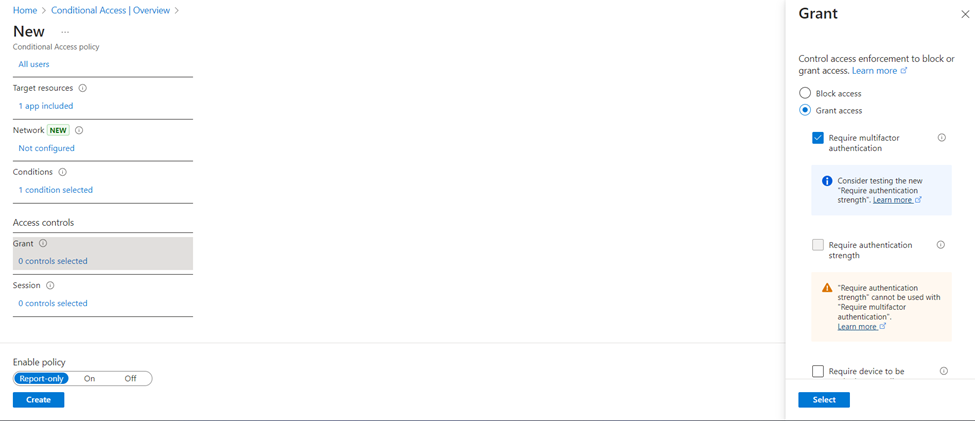
- In this example, we will apply the MFA policy on Android, IOS, Windows, and macOS platforms. This policy will help us verify who wants to access the mail and increase security.
Overall, Office 365 Conditional Access is a critical tool for organizations looking to secure their cloud environments by implementing intelligent, adaptive access controls that align with their security requirements and user productivity needs.
Untill next time.
Abdelrahman Kassem
System Engineer