Today, companies struggle to control and govern increasingly complex environments that extend across data centers, multiple clouds, and edge. Each environment and cloud possesses its own set of management tools, and new DevOps and ITOps operational models can be hard to implement across resources.
Azure Arc simplifies governance and management by delivering a consistent multicloud and on-premises management platform.
Azure Arc provides a centralized, unified way to:
- Manage your entire environment together by projecting your existing non-Azure and/or on-premises resources into Azure Resource Manager.
- Manage virtual machines, Kubernetes clusters, and databases as if they are running in Azure.
- Use familiar Azure services and management capabilities, regardless of where your resources live.
- Continue using traditional ITOps while introducing DevOps practices to support new cloud native patterns in your environment.
- Configure custom locations as an abstraction layer on top of Azure Arc-enabled Kubernetes clusters and cluster extensions.
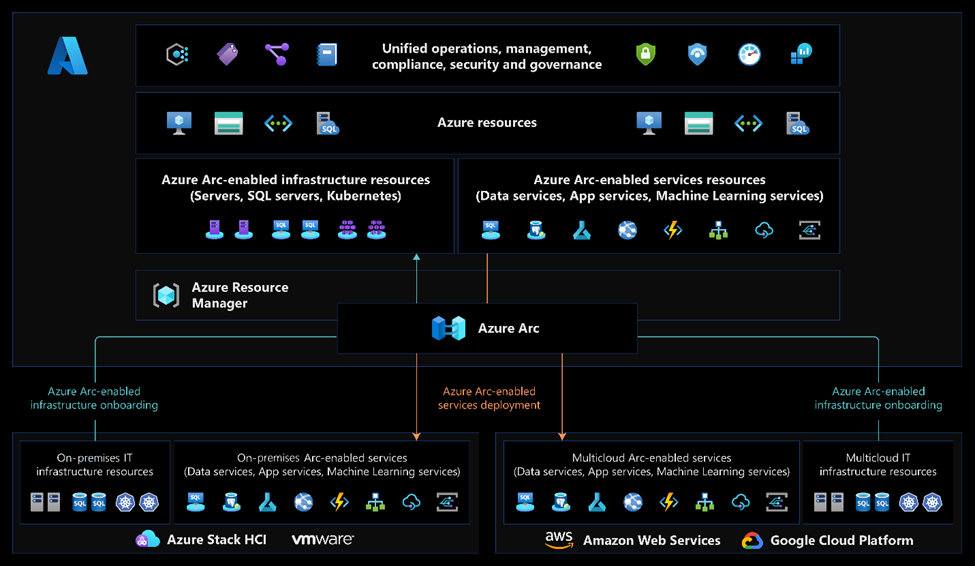
Currently, Azure Arc allows you to manage the following resource types hosted outside of Azure:
- Servers: Manage Windows and Linux physical servers and virtual machines hosted outside of Azure.
- Kubernetes clusters: Attach and configure Kubernetes clusters running anywhere, with multiple supported distributions.
- Azure data services: Run Azure data services on-premises, at the edge, and in public clouds using Kubernetes and the infrastructure of your choice. SQL Managed Instance and PostgreSQL (preview) services are currently available.
- SQL Server: Extend Azure services to SQL Server instances hosted outside of Azure.
- Virtual machines: Provision, resize, delete and manage virtual machines based on VMware vSphere or Azure Stack HCI and enable VM self-service through role-based access.
In the Previous post we talked about Onboarding onprem Kubernetes cluster and using Azure Policy to check for compliance according to the required policy.
Today we’re going to talk about Azure Data services and deploying SQL Managed Instance on your datacenter. This feature allows you to Run Azure data services on any Kubernetes environment as if it runs in Azure (specifically Azure SQL Managed Instance and Azure Database for PostgreSQL server, with benefits such as upgrades, updates, security, and monitoring). Use elastic scale and apply updates without any application downtime, even without continuous connection to Azure.
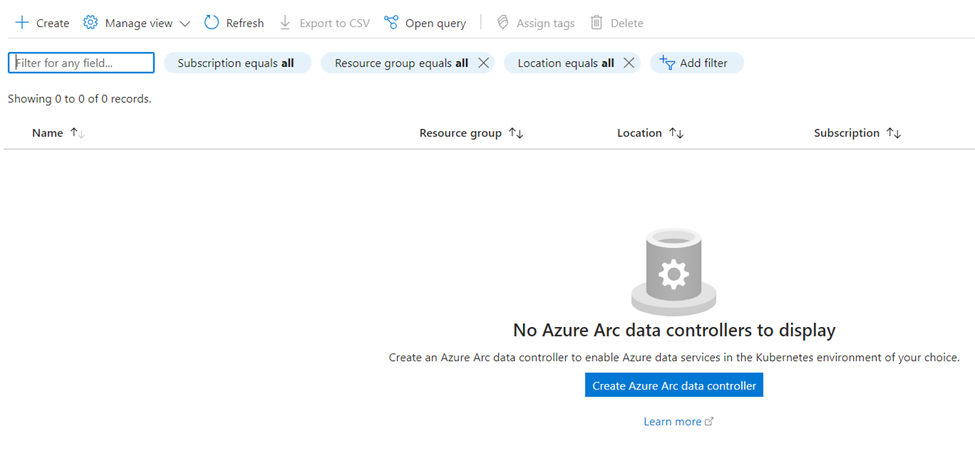
Create Azure Arc data controller in direct connectivity mode using Portal
Azure Arc data controller create flow can be launched from the Azure portal in one of the following ways:
- From the search bar in Azure portal, search for “Azure Arc data controllers”, and select “+ Create”
- From the Overview page of your Azure Arc-enabled Kubernetes cluster,
- Select “Extensions ” under Settings.
- Select “Add” from the Extensions overview page and then select “Azure Arc data controller”
- Select Create from the Azure Arc data controller marketplace gallery
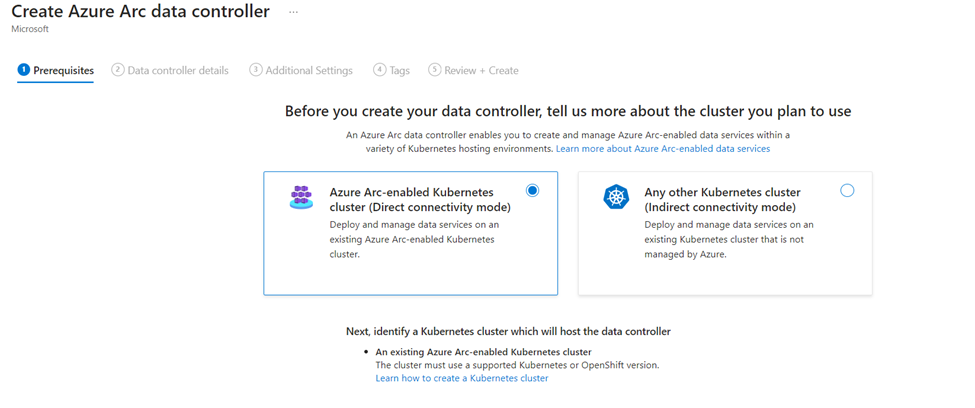
- Ensure the Azure Arc-enabled Kubernetes cluster (Direct connectivity mode) option is selected. Select “Next : Data controller details”
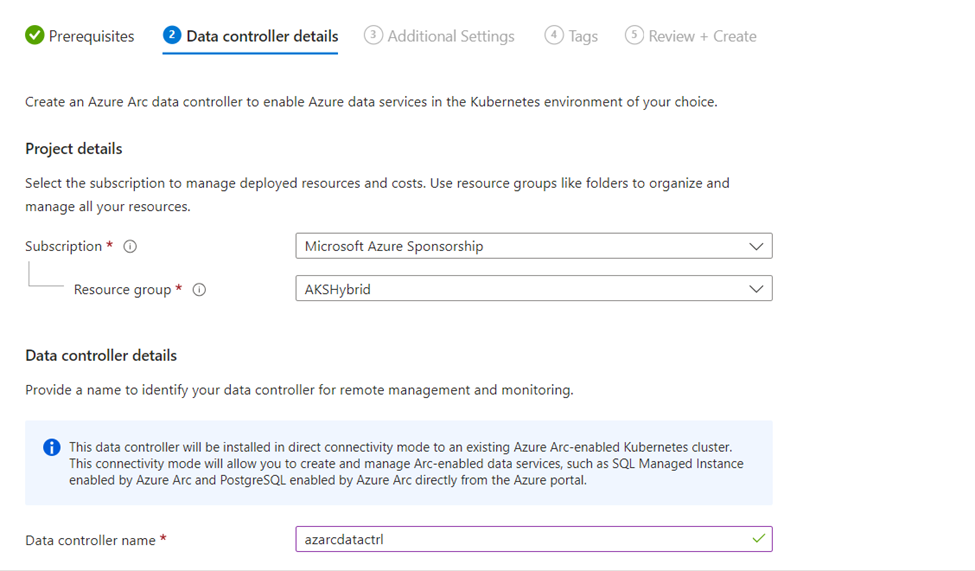
- In the Data controller details page:
- Select the Azure Subscription and Resource group where the Azure Arc data controller will be projected to.
- Enter a name for the Data controller
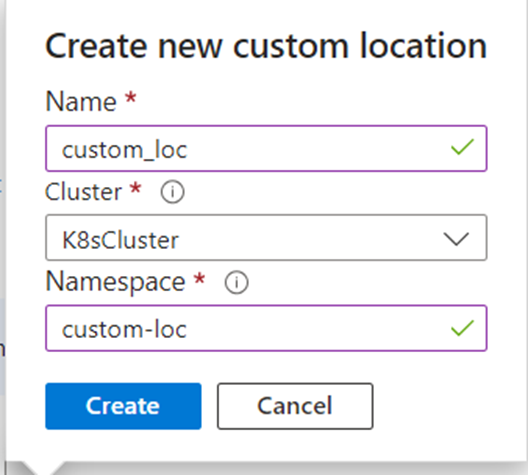
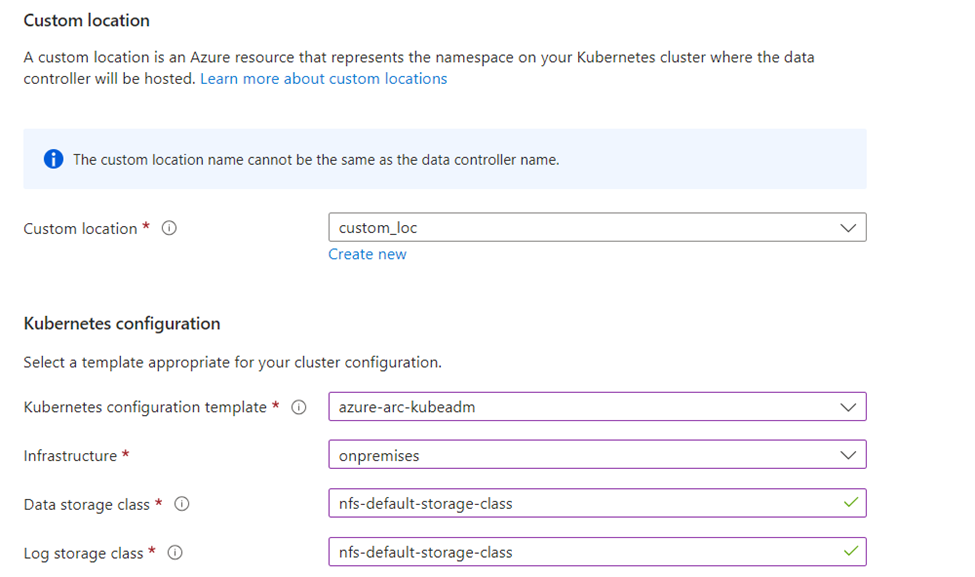
- Select a pre-created Custom location or select “Create new” to create a new custom location. If you choose to create a new custom location, enter a name for the new custom location, select the Azure Arc-enabled Kubernetes cluster from the dropdown, and then enter a namespace to be associated with the new custom location, and finally select Create in the Create new custom location window. Learn more about custom locations
- Kubernetes configuration – Select a Kubernetes configuration template that best matches your Kubernetes distribution from the dropdown. If you choose to use your own settings or have a custom profile you want to use, select the Custom template option from the dropdown. In the blade that opens on the right side, enter the details for Docker credentials, repository information, Image tag, Image pull policy, infrastructure type, storage settings for data, logs and their sizes, Service type, and ports for controller and management proxy. Select Apply when all the required information is provided. You can also choose to upload your own template file by selecting the “Upload a template (JSON) from the top of the blade. If you use custom settings and would like to download a copy of those settings, use the “Download this template (JSON)” to do so. Learn more about custom configuration profiles.
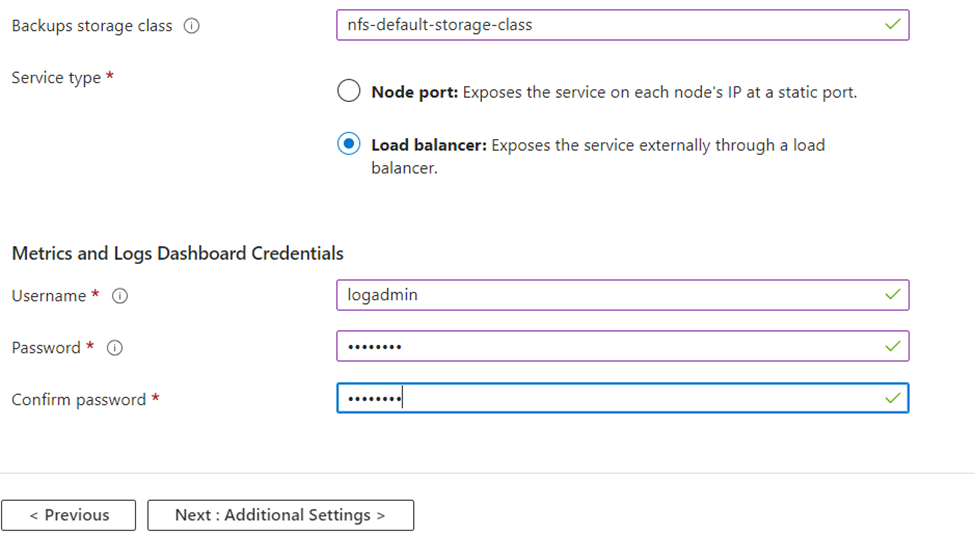
- Select the appropriate Service Type for your environment
- Metrics and Logs Dashboard Credentials – Enter the credentials for the Grafana and Kibana dashboards
- Select the “Next: Additional settings” button to proceed forward after all the required information is provided.
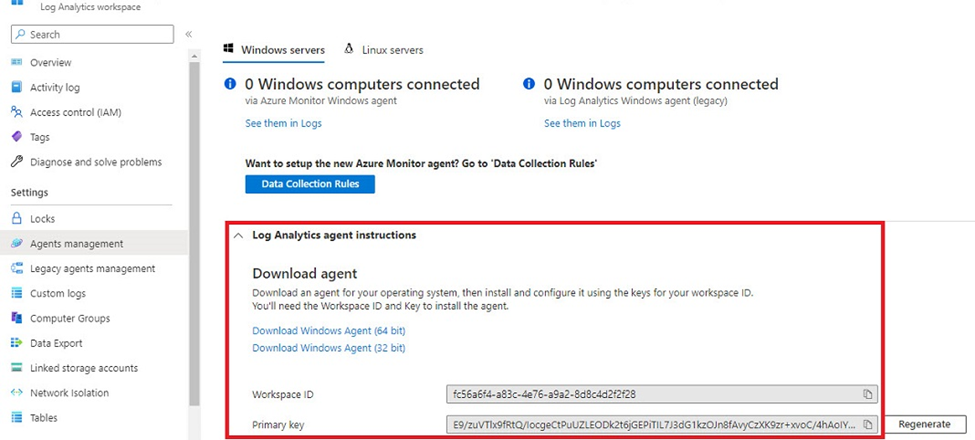
To check for Log analytics Primary key:
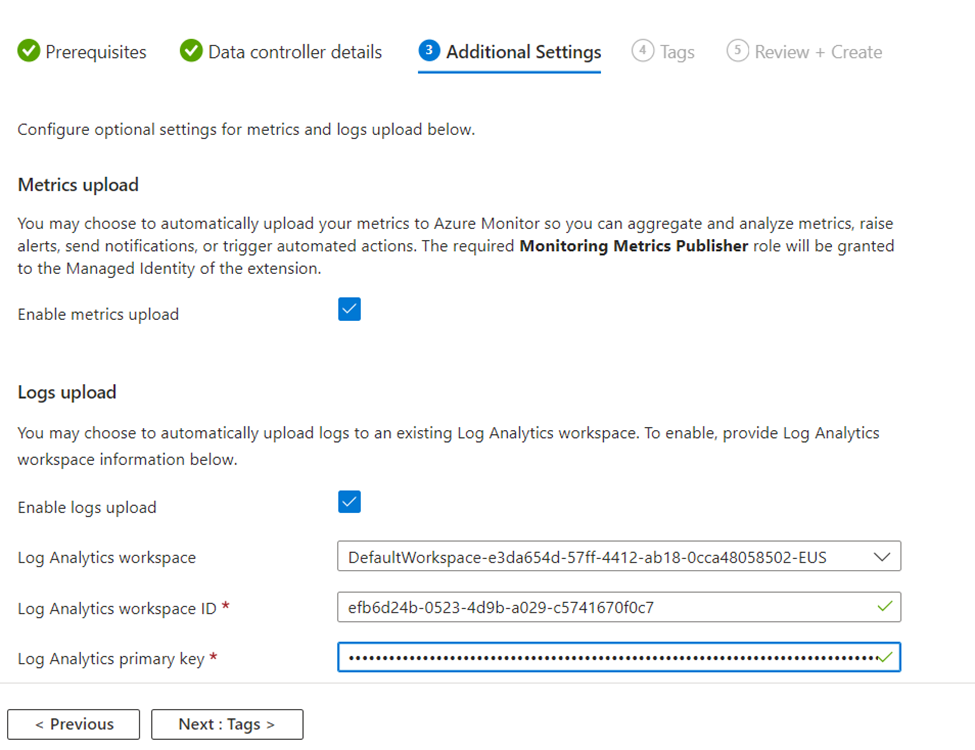
- In the Additional Settings page:
- Metrics upload: Select this option to automatically upload your metrics to Azure Monitor so you can aggregate and analyze metrics, raise alerts, send notifications, or trigger automated actions. The required Monitoring Metrics Publisher role will be granted to the Managed Identity of the extension.
- Logs upload: Select this option to automatically upload logs to an existing Log Analytics workspace. Enter the Log Analytics workspace ID and the Log analytics shared access key.
- Select “Next: Tags” to proceed.
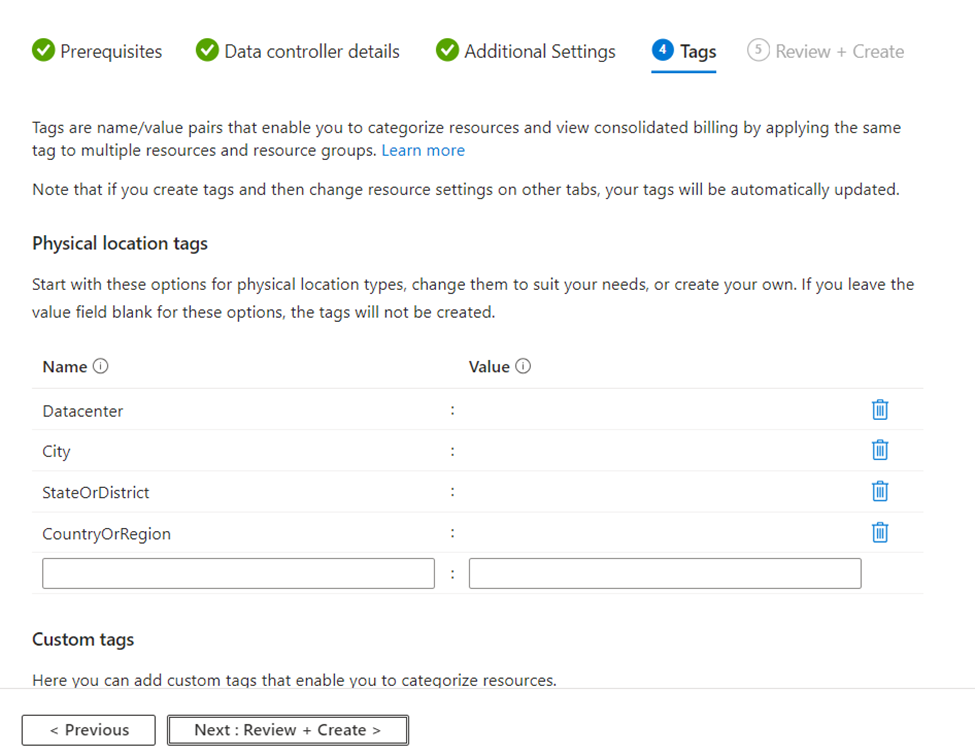
- In the Tags page, enter the Names and Values for your tags and select “Next: Review + Create”.
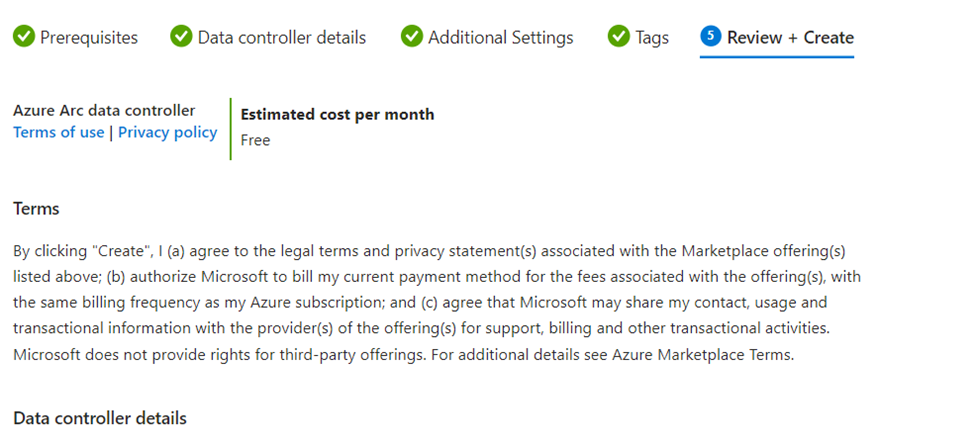
- In the Review + Create page, view the summary of your deployment. Ensure all the settings look correct and select “Create” to start the deployment of Azure Arc data controller.
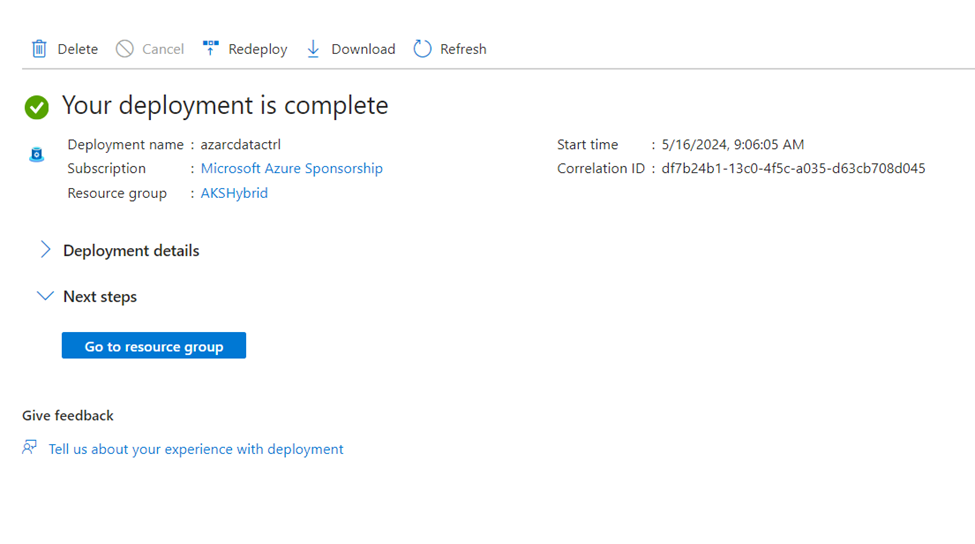
That’s it for Part 1, in part 2 we’ll proceed with creating a new SQL Managed Instance.
I hope this was informative for you, please let me know your comments.
See you soon
Karim Hamdy
Infrastructure Architect

