What is Threat Intelligence anyway?
The first time I heard the term Threat Intelligence I was a little baffled, what is that anyway? Why should I care about it? Interestingly it is a very useful tool that helps Cyber Security teams or SecOps Analyst to stay on top of their game.
Throughout the challenging environment and adversaries around the world that are adapting rapidly to every measure that has been put to counter any threats, arises a very important question, how do we keep up with the nature of this field that has everyday something new or some attack that has been spreading like fire.
In 2017 particularly May 12th everyone woke up to the news of a new threat or attack called WannaCry and indeed it caused many IT & Security and even business teams cry! We suddenly realized we are no longer protected by these firewalls, Antivirus installed on our computers.
What makes WannaCry special is it was some sort of weapon rather than a normal computer virus; it paved the way for criminals that “Hey! We can make money from this!”
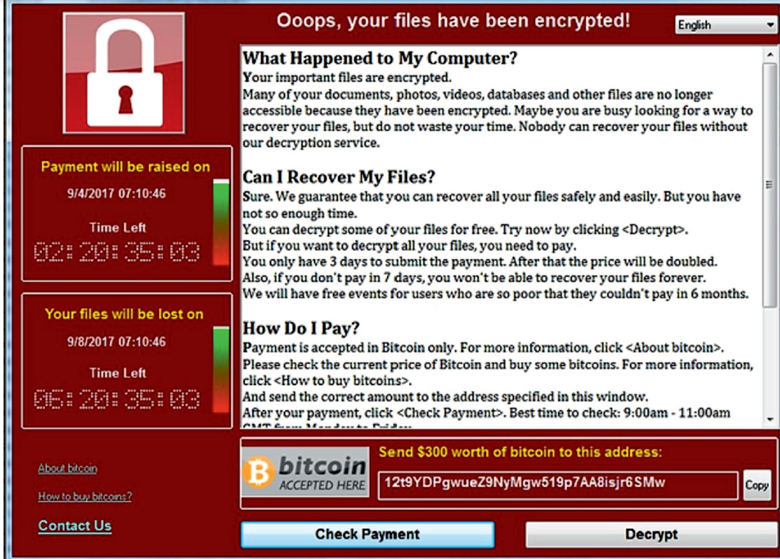
On the technical level the attack itself had some interesting concepts that materialized like persistence to be in your environment, evading defenses and reconnaissance.
At the time of the attack there was no reliable source of information on how to handle such attack or what countermeasures should we deploy to try and stop this from getting into our systems and environment.
That’s when Threat Intelligence comes along, it is like your special detective that tells you Roger Rabbit has been framed and here is the proof! Here are some benefits of using TI in your environment:
Threat actors
A threat actor refers to an entity or individual responsible for carrying out malicious activities or cyberattacks against organizations or individuals. Threat actors can range from individual hackers to organized cybercrime groups, nation-state actors, and even insiders with malicious intent. Understanding threat actors is crucial for effective threat intelligence analysis and cybersecurity defense strategies.
Tooling
Tooling in Threat Intelligence encompasses a comprehensive suite of tools, platforms, and technologies that empower security teams to collect, analyze, manage, and operationalize threat intelligence effectively. By leveraging advanced tooling capabilities, organizations can strengthen their cybersecurity defenses, improve incident response capabilities, and stay ahead of evolving cyber threats.
Attack
Refers to ongoing attacks or campaign that has been going on lately.
Vulnerabilities
refer to weaknesses or flaws in software, hardware, or configurations that can be exploited by threat actors to compromise systems, steal data, or disrupt operations.
Indicators
indicators refer to pieces of information or data that serve as evidence or signals of potential cyber threats. These indicators, often referred to as indicators of compromise (IOCs), help security teams identify, detect, and respond to malicious activities and security incidents. Threat Intelligence utilizes various types of indicators to enhance threat detection and improve cybersecurity defenses.
Here are the key types of indicators used in Threat Intelligence:
- File Hashes: File hashes, such as MD5, SHA-1, and SHA-256, are unique cryptographic representations of files. Threat Intelligence collects and analyzes file hashes associated with known malware, suspicious files, and malicious executables. File hashes serve as indicators of potential malware infections and are used in threat detection and incident response workflows.
- IP Addresses: IP addresses associated with malicious activities, command and control (C2) servers, botnets, and malicious domains are tracked and categorized Threat Intelligence. These IP addresses serve as indicators of malicious infrastructure and are used to block malicious traffic, identify compromised systems, and enhance network security controls.
- Domain Names: Malicious domain names, phishing domains, typosquatting domains, and other suspicious URLs are monitored and categorized as indicators in Threat Intelligence. These domain names serve as indicators of malicious websites, phishing campaigns, and malicious URLs used in cyber attacks. Blocking or blacklisting these domains helps prevent users from accessing malicious content.
- URLs: URLs associated with malicious activities, phishing attacks, drive-by downloads, and exploit kits are tracked and analyzed as indicators in Threat Intelligence. These URLs serve as indicators of malicious web traffic and are used to block access to malicious websites, detect phishing attempts, and protect users from web-based threats.
- Malware Signatures: Malware signatures, including patterns of code, behaviors, and characteristics unique to specific malware families, are collected and categorized in Threat Intelligence. These signatures serve as indicators of known malware infections and are used in malware detection, signature-based scanning, and threat intelligence analysis.
- Email Addresses: Malicious email addresses, phishing email senders, spoofed email domains, and known malicious email campaigns are tracked and categorized as indicators in Threat Intelligence. These email addresses serve as indicators of phishing attempts, malicious attachments, and email-based threats targeting organizations.
- Behavioral Indicators: Behavioral indicators, such as abnormal network traffic patterns, anomalous user behavior, suspicious system activities, and indicators of lateral movement, are monitored and analyzed in Threat Intelligence. These behavioral indicators serve as early warning signs of potential security incidents and are used in anomaly detection, threat hunting, and incident response.
Imagine if you have this knowledge in 2017, WannaCry wouldn’t have done so much damage back then! You could use these kind of information to your benefit and stop the attack once it reaches your door.
You would be informed immediatly of the attack and what’s happening around the world, rather than waiting for a catastrophe to happen.
So to sum up, Threat Intelligence Platforms gives you the following benefits:
Here are some key aspects of threat intelligence:
- Data Collection: Threat intelligence teams gather data from a wide range of sources, including:
- Internal sources such as security logs, network traffic, and endpoint telemetry.
- External sources such as open-source intelligence (OSINT), threat feeds, security vendors, government agencies, and information-sharing communities.
- Dark web monitoring to identify discussions, forums, and marketplaces related to cyber threats.
- Data Analysis: Once data is collected, it’s analyzed to identify patterns, trends, and potential threats. This analysis involves:
- Correlating and contextualizing data to understand the threat landscape.
- Identifying indicators of compromise (IOCs), tactics, techniques, and procedures (TTPs) used by threat actors.
- Classifying threats based on severity, relevance to the organization, and potential impact.
- Information Sharing: Threat intelligence is often shared within organizations and across industry sectors through information-sharing platforms and communities. Sharing intelligence helps to:
- Improve collective defense by providing early warnings and insights into new threats.
- Enhance incident response capabilities by sharing actionable intelligence with security teams.
- Collaborate with peers, partners, and authorities to mitigate cyber threats effectively.
- Threat Intelligence Feeds: These are curated streams of threat data provided by security vendors, research organizations, and government agencies. Threat intelligence feeds can include:
- IP addresses, domains, and URLs associated with malicious activity.
- Malware signatures, file hashes, and indicators of compromise (IOCs).
- Information about threat actors, their tactics, and infrastructure.
- Cyber Threat Intelligence (CTI) Platforms: These are tools and platforms used to manage, analyze, and operationalize threat intelligence. CTI platforms provide capabilities such as:
- Automated data ingestion and normalization from various sources.
- Visualization of threat data through dashboards, reports, and heat maps.
- Integration with security technologies for automated threat response and enrichment.
- Strategic decision-making and risk management to align security investments with the organization’s threat landscape.
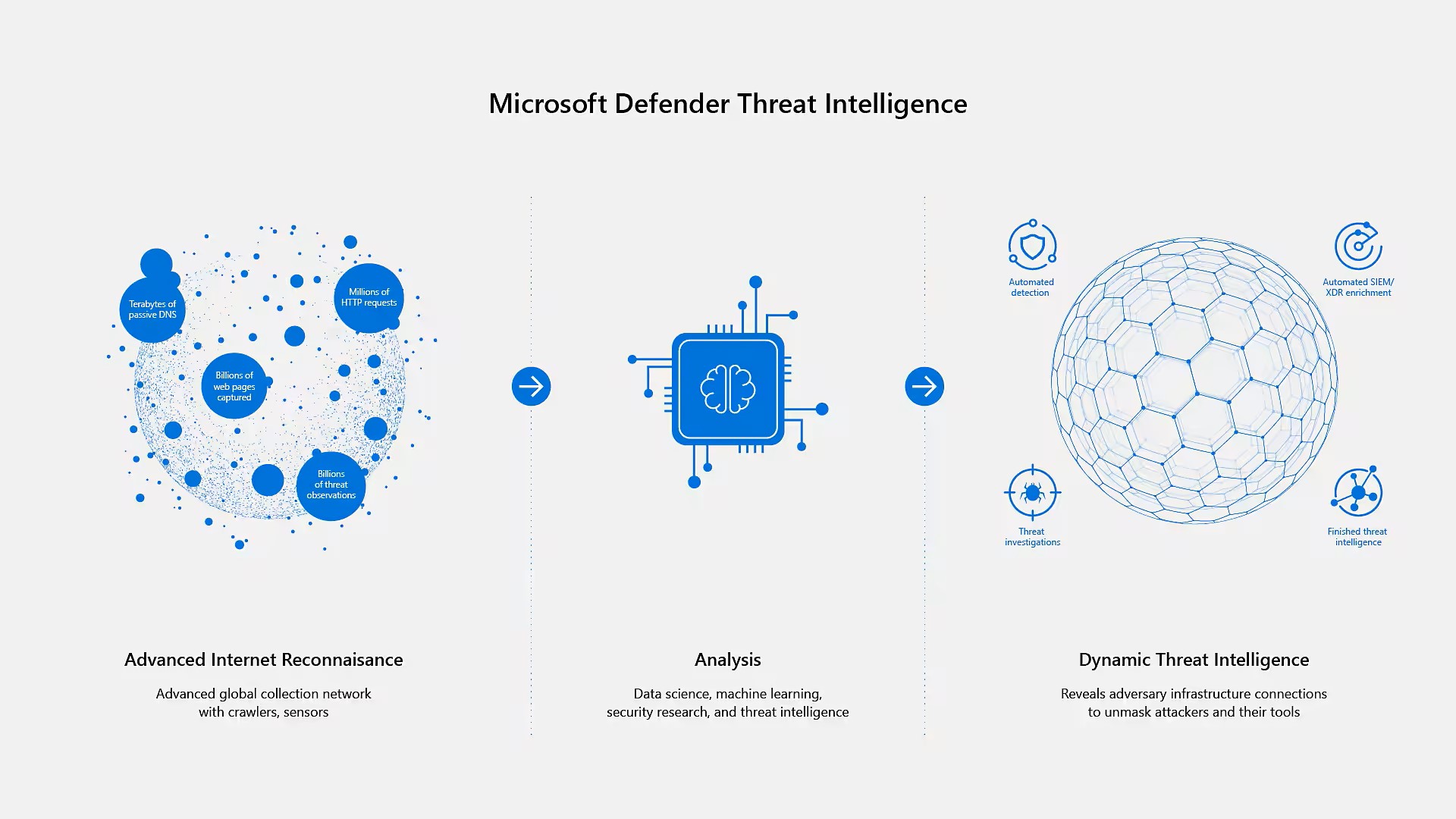
In Part two we’ll talk about Microsoft Defender Threat Intelligence Platform
So Stay Tuned!
For more info on the famous WannaCry attack, you can view the following Document:
https://www.researchgate.net/publication/332088162_WannaCry_Ransomware_Analysis_of_Infection_Persistence_Recovery_Prevention_and_Propagation_Mechanisms
Let me hear your thoughts in the comments. Till we meet again!
Karim Hamdy